PingOne Protect
The PingOne Protect service provides capabilities to configure and retrieve risk evaluations from internal and external risk providers based on a specified risk policy.
Refer also to PingOne Protect's integration with Ping Gateway for on-premise use of PingOne Protect with web applications protected by PingGateway.
Risk Policies
A risk policy is determined by your specific configuration settings. The risk policy enables you to customize a risk evaluation to fit your use case. The policy is used during a risk evaluation to calculate the risk scores for received events. For more information about risk policies, refer to Risk Policies.
Risk Evaluations
Use risk evaluations to calculate the risk level and other risk-related details associated with a received event based on the environment's settings and data provided in the event. For more information about risk evaluation, refer to Risk Evaluations.
Risk Predictors
Risk predictors are employed by risk policies, and define thresholds for certain criteria (such as, IP Velocity, User Velocity, or User Location Anomaly) to determine whether there's the potential for fraudulent user behavior. For more information refer to Risk Predictors.
Use Cases
Risk Policies
Risk policies enable you to customize the risk evaluations to your specific needs. Risk policies are containers for specific risk logic. You can define multiple risk policies and deploy them to initiate different authentication flow actions based on the calculated risk. By default, every PingOne environment has an associated system-level default risk policy set.
For more information about the default risk policies, refer to the example response in Read Risk Policy Sets. Each risk policy set contains a list of risk policies. The maximum number of policy sets per environment is 100; the maximum number of policies per policy set is 100.
Risk policies have the components:
-
Condition
A Boolean predicate that defines when the policy element is evaluated to true and when it is evaluated to false.
-
Result
Defines the final result of the risk evaluation when the condition is evaluated to true.
Value comparison conditions
Value comparison conditions compare a placeholder to a value. For example:
{
"value": "${some.placeholder}",
"equals": "some value"
}
The value is the outcome of one of the risk predictors.
IP range conditions
IP range conditions designate IP addresses for whitelisting and blacklisting.
{
"ipRange": ["1.1.1.1/16", "2.2.2.2/24"],
"contains": "${transaction.ip}"
}
Override policies
Override policies are the ones with the highest priority. They should be listed at the beginning of the riskPolicies array. They can have value comparison condition rules or IP range condition rules. The risk policy array can have no override policies or multiple override policies.
Combining predictors
There are two methods of combining the predictors - Weights and Scores. When you use the Weights approach, you are determining relative weights that should be used when calculating the individual risk score for each predictor. When you use the Scores approach, you can exercise more control over the overall calculation because you can specify an exact numerical score that should be assigned when PingOne Protect determines that there is a medium or high risk level for a predictor.
Weighted policies
Weighted policies allow you to combine results from multiple predictors.
Weighted policies determine risk based on aggregated weighted risk score. These policies must be listed in the riskPolicies array after all override policies are specified. An aggregated risk score involves two weighted policies, and these policies must be the last policies in the riskPolicies array.
The weighted policies that determine the aggregated risk score complement each other and are subject to these restrictions:
-
The first weighted policy should have
result.level=MEDIUMand the second should haveresult.level=HIGH. -
The value for the
condition.aggregatedWeightsattribute for both policies must be the same. -
The value for the
condition.between.maxScoreattribute for theHIGHweighted policy must be 100. -
The value of the
condition.betweenattribute for the two policies must be complementary. For example, if theHIGHpolicy hascondition.between.minScore = 70, theMEDIUMpolicy should havecondition.between.maxScore = 70. -
condition.typeshould be set to AGGREGATED_WEIGHTS. -
Choose the
weightvalue assigned to each predictor outcome according to its significance. The following example shows theweightfor two predictors:ipAddressReputationat 9 and theweightforgeoVelocityat 4. The maximum and minimum scores are set at 60 and 90, respectively:
{
"aggregatedWeights": [
{
"value": "${details.aggregatedWeights.ipAddressReputation}",
"weight": 9
},
{
"value": "${details.aggregatedWeights.geoVelocity}",
"weight": 4
}
],
"between": {
"minScore": 60,
"maxScore": 90
}
}
The value of value consists of the identifier for a specific predictor, and it takes the form ${details.aggregatedWeights.geoVelocity}, where the string after aggregatedWeights is the compact name of the relevant predictor.
Score policies
The JSON content below shows an example of a policy set that uses the Scores approach to risk calculation.
Details to note about the use of score policies:
-
If you are including overrides in the policy set, they must precede the score policies.
-
The policy set must include two score policies - one that includes the score range that should be translated into MEDIUM risk, and one that includes the score range that should be translated into HIGH risk.
-
In terms of order, the MEDIUM policy must precede the HIGH policy.
-
Use
condition.between.minScoreandcondition.between.maxScoreto define the ranges for MEDIUM risk and HIGH risk. ThemaxScorefor MEDIUM risk should always equal theminScorefor HIGH risk. -
condition.typeshould be set to AGGREGATED_SCORES. -
The
conditionobject should contain anaggregatedScoresobject that consists of an array ofvalue/scorepairs. The value ofvalueconsists of the identifier for a specific predictor, and it takes the form${details.userLocationAnomaly.level}, where the string betweendetailsandlevelis the compact name of the relevant predictor. The value ofscoreis the score you want to assign to that predictor when it is determined that there is a high risk for the predictor. If it is determined that there is medium risk, the predictor will automatically be assigned a score equal to half of the value you specified for high risk. -
The array in
condition.aggregatedScoresmust be identical in the MEDIUM policy that you define and the HIGH policy that you define.
{
"id": "944fa7b4-e280-4932-80e7-01853ac9ce6d",
"name": "aa",
"default": false,
"defaultResult": {
"level": "Low"
},
"riskPolicies": [
{
"name": "ANONYMOUS_NETWORK_DETECTION",
"result": {
"level": "HIGH"
},
"condition": {
"value": "${details.anonymousNetworkDetected}",
"equals": true
}
},
{
"name": "GEOVELOCITY_ANOMALY",
"result": {
"level": "MEDIUM"
},
"condition": {
"value": "${details.impossibleTravel}",
"equals": true
}
},
{
"name": "Medium score policy",
"result": {
"level": "MEDIUM"
},
"condition": {
"type" : "AGGREGATED_SCORES",
"aggregatedScores": [
{
"value": "${details.userLocationAnomaly.level}",
"score": 40
},
{
"value": "${details.anonymousNetwork.level}",
"score": 60
},
{
"value": "${details.ipRisk.level}",
"score": 40
}
],
"between": {
"minScore": 700,
"maxScore": 900
}
}
},
{
"name": "High score policy",
"result": {
"level": "HIGH"
},
"condition": {
"type" : "AGGREGATED_SCORES",
"aggregatedScores": [
{
"value": "${details.userLocationAnomaly.level}",
"score": 40
},
{
"value": "${details.anonymousNetwork.level}",
"score": 60
},
{
"value": "${details.ipRisk.level}",
"score": 40
}
],
"between": {
"minScore": 900,
"maxScore": 1000
}
}
}
]
}
Condition type
The condition.type field indicates the type of policy you are defining. It can take any of the following values:
- AGGREGATED_SCORES
- AGGREGATED_WEIGHTS (deprecated)
- VALUE_COMPARISON
- IP_RANGE (for override policies or custom predictors)
Risk staging policy set
Risk staging policy allows you to test a policy set in parallel with another policy set. You link an existing policy set to the test policy set with a triggers object in the existing policy set, which points to the test policy set in its triggers.policySet object. Every time the existing policy set runs, it triggers the test policy set to also run. While in staging, the test policy set runs but only records its evaluation. A trigger expires 3 months from when it is set. Use Update Risk Policy Set to add the triggers object to an existing policy set.
Targeted risk policies
For standard risk policies, you must choose the risk policy to pass to the risk evaluation. Targeted risk policies allow you to define risk policies for different "targets" - combinations of transaction types, user groups, and applications that are being accessed. You can then order the targeted risk policies that you defined. When a risk evaluation is carried out, these targeted policies are processed in the order that you specified. The risk policy that is ultimately used for the risk evaluation will be the first one whose conditions (transaction type, user group, application) are met.
The following JSON snippet shows how to specify the target for a risk policy. For details, refer to the targets object in the Risk policies data model and the Create Risk Policy Set - Targeted Policy with Mitigations example.
"targets":{
"condition": { "and": [{
"list": ["AUTHENTICATION", "AUTHORIZATION"],
"contains": "${event.flow.type}"
},
{
"list": ["Sales"],
"contains": "${event.user.groups}"
},
{
"list": ["6b6f867b-d768-4c2c-a9b6-6816da00d824", "845c9918-94d7-430c-b3d8-eafafc215fd9"],
"contains": "${event.targetResource.id}"
}]
}
}
Using mitigations in your policies
You can choose to include mitigations in your risk policies. In this context, a mitigation is an action that you recommend if a given condition is met, for example, deny access if the email reputation predictor indicates high risk. In situations where the condition is met, the action that you recommended be taken is returned in the risk evaluation response as the value of the result.mitigations[].action field.
The following JSON snippet shows how to define mitigations in a risk policy (within the riskPolicies array). For details, refer to the result.mitigations array in the Risk policies data model and the Create Risk Policy Set - Targeted Policy with Mitigations example.
{
"name" : "USER_LOCATION_ANOMALY",
"result" : {
"mitigations" : [ {
"action" : "CUSTOM",
"customAction" : "CustomActionForUserLocationAnomaly"
}],
"type" : "MITIGATION"
},
"condition" : {
"value" : "${details.userLocationAnomaly.level}",
"equals" : "High",
"type" : "VALUE_COMPARISON"
}
},
{
"name" : "VELOCITY",
"result" : {
"mitigations" : [ {
"action" : "DENY_AND_SUSPEND"
} ],
"type" : "MITIGATION"
},
"condition" : {
"value" : "${details.ipVelocityByUser.level}",
"equals" : "High",
"type" : "VALUE_COMPARISON"
}
},{
"name" : "USER_RISK_BEHAVIOR",
"result" : {
"mitigations" : [ {
"action" : "VERIFY"
} ],
"type" : "MITIGATION"
},
"condition" : {
"value" : "${details.userBasedRiskBehavior.level}",
"equals" : "Medium",
"type" : "VALUE_COMPARISON"
}
},
{
"name" : "EMAIL_REPUTATION",
"result" : {
"mitigations" : [ {
"action" : "MFA",
"mfaAuthenticationPolicyId" : "{{deviceAuthenticationPolicyID}}"
} ],
"type" : "MITIGATION"
},
"condition" : {
"value" : "${details.emailReputation.level}",
"equals" : "High",
"type" : "VALUE_COMPARISON"
}
},
{
"name" : "IP_REPUTATION",
"result" : {
"mitigations" : [ {
"action" : "APPROVE"
} ],
"type" : "MITIGATION"
},
"condition" : {
"value" : "${details.ipRisk.level}",
"equals" : "Low",
"type" : "VALUE_COMPARISON"
}
}
Base risk policy set data model
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
createdAt |
Date | N/A | Read-only | The date and time the resource was created (format ISO-8061). |
default |
Boolean | Optional | Mutable | Indicates whether this risk policy set is the environment's default risk policy set. This is used whenever an explicit policySet ID is not specified in the risk evaluation request. If this property is not specified when you create or update a risk policy, the value defaults to false, and this risk policy set is not regarded as the default risk policy set for the environment. If you set this property to true, the default property of all other risk policies in the environment is set to false. |
defaultResult |
Object | Optional | Mutable | Contains the default result returned if none of the conditions in the policy are evaluated to true. At this time, the defaultResult.level value must be LOW. |
description |
String | Optional | Mutable | A description for this policy set. Valid characters consist of any Unicode letter, mark (for example, accent, umlaut), numeric character, punctuation character, or space. Maximum size is 1024 characters. |
environment.id |
String | Required | Immutable | The environment resource's unique identifier. |
evaluatedPredictors |
Array | N/A | Read-only | The IDs of the risk predictors that are evaluated in the policy. Included in responses to requests to get risk policies. |
id |
String | Required | Immutable | The resource's unique identifier. |
name |
String | Required | Mutable | The name for this policy set. Valid characters consist of any Unicode letter, mark (such as, accent, umlaut), # (numeric), / (forward slash), . (period), ' (apostrophe), _ (underscore), space, or - (hyphen). Maximum size is 256 characters. |
riskPolicies |
Array | Required | Mutable | The conditions associated with this policy set. Refer also to [Risk policies data model]{#risk-policies-data-model} below. |
riskPolicySetTargets.user.matchedGroups |
Array | N/A | Read-only | The user groups specified in the policy target that the current user belongs to. |
riskPolicySetTargets.user.matchedGroups[].name |
String | N/A | Read-only | The name of the user group. |
targetedRiskPolicySetsOrder |
Array | Optional | Mutable | The targetedRiskPolicySetsOrder array represents the order that was defined for the processing of targeted risk policies in the environment. It contains the IDs of the individual targeted policies. This array is included in the response when you read one or all risk policies and include the expand query parameter set to order in the URL. You can also use targetedRiskPolicySetsOrder to specify a new order for the targeted policies, refer to the [Reorder Targeted Risk Policies]((#post-reorder-targeted-risk-policies) example. |
triggers |
Object[] | Optional | Mutable | Array that contains trigger definitions for staging mode. |
triggers.type |
String | Required | Immutable | Trigger type; must be POLICY_SET_STAGING. |
triggers.policySet |
Object | Required | Immutable | Contains the policy set identifier to trigger. |
triggers.policySet.id |
String | Required | Immutable | UUID of the policy set to trigger in staging mode. |
triggers.expiresAt |
String | Required | Immutable | Date and time at which the trigger expires. |
updatedAt |
Date | N/A | Read-only | The date and time the resource was last updated (format ISO-8061). |
Risk policies data model
This table lists the fields and objects that can be included in each of the elements in the riskPolicies array.
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
condition |
Object | Required | Mutable | Contains the condition logic that determines when a policy is evaluated to true and when it is evaluated to false. |
condition.aggregatedScores |
Array | Required/Optional | Mutable | Required for score-based policies. The elements in the array are value-score pairs, representing the score that should be assigned to a specific predictor when it is determined that there is a high risk for the predictor. |
condition.aggregatedScores.value |
String | Required | Mutable | Text that identifies a specific risk predictor in the environment. It uses the form ${details.xxxxxxx.level}, where the string between details and level is the compact name of the relevant predictor. |
condition.aggregatedScores.score |
Integer | Required | Mutable | The score you want to assign to the predictor when it is determined that there is a high risk for the predictor. Value should be between 0 and 100. If it is determined that there is medium risk, the predictor will automatically be assigned a score equal to half of the value you specified for high risk. |
condition.value |
String | Optional | Mutable | When defining an override or mitigation, use condition.value to specify the predictor attribute that is checked for the value specified with the condition.equals parameter, for example, ${details.userLocationAnomaly.level}. |
condition.equals |
String | Optional | Mutable | When defining an override or mitigation, use condition.equals to specify the risk level that the condition is looking for when checking the predictor that you specified with condition.value. For risk predictors with three levels, the value of equals should be High, Medium, or Low. For boolean risk predictors, such as anonymous network detection. the value of equals should be true or false. |
condition.type |
String | Required | Mutable | Indicates the type of policy you are defining. Can be one of the following values: AGGREGATED_SCORES, AGGREGATED_WEIGHTS (deprecated), VALUE_COMPARISON, and IP_RANGE (for override policies or custom predictors). |
condition.between.minScore |
Integer | Required/Optional | Mutable | Required for policies of type AGGREGATED_SCORES or AGGREGATED_WEIGHTS. The beginning of the risk score range that will be translated into the specified risk level (MEDIUM or HIGH). Must be between 0 and 1000. |
condition.between.maxScore |
Integer | Required/Optional | Mutable | Required for policies of type AGGREGATED_SCORES or AGGREGATED_WEIGHTS. The end of the risk score range that will be translated into the specified risk level (MEDIUM or HIGH). Must be between 0 and 1000. |
createdAt |
Date | Required | Immutable | The date and time the resource was first created (format ISO-8061). |
description |
String | Optional | Mutable | A description for this risk policy. Valid characters consist of any Unicode letter, mark (for example, accent, umlaut), # (numeric), / (forward slash), . (period), ' (apostrophe), _ (underscore), space, or - (hyphen). Maximum size is 1024 characters. |
environment.id |
String | Required | Immutable | The environment resource's unique identifier. |
id |
String | Required | Immutable | The resource’s unique identifier. |
name |
String | Required | Mutable | The name to use for the condition. Valid characters consist of any Unicode letter, mark (for example, accent, umlaut), # (numeric), / (forward slash), . (period), ' (apostrophe), _ (underscore), space, or - (hyphen). Maximum size is 256 characters. |
priority |
Integer | N/A | Read-only | The index of the element in the riskPolicies array. |
result |
Object | Required | Mutable | The result object is used to specify the risk level that should be assigned if the defined condition is met. When defining mitigations, result is used to specify the action that is being recommended. |
result.level |
String | Required | Mutable | Contains the risk level that is returned if the condition is evaluated as true. If several policies are evaluated as true, the result related to the lowest priority condition is returned. For more information, refer to the Result attribute data model in Risk Evaluations. |
result.mitigations |
Array | Optional | Mutable | For mitigations that you define, contains the action that is being recommended if the specified condition is met. |
result.mitigations[].action |
String | Required | Mutable | The action that is being recommended if the condition specified for the mitigation is met. Can take any of the following values: APPROVE, VERIFY, MFA, DENY, DENY_AND_SUSPEND, CUSTOM. If you set action to MFA, use mfaRegistrationPolicyId and mfaAuthenticationPolicyId to specify the IDs of the MFA registration policy and MFA authentication policy that should be used. If you set action to VERIFY, use verifyPolicyId to specify the ID of the Verify policy that should be used. If you set action to CUSTOM, use customAction to specify the custom action that you want to recommend. |
result.mitigations[].customAction |
String | Optional | Mutable | If you set the action parameter to CUSTOM, use customAction to specify the custom action that you want to recommend. |
result.mitigations[].mfaAuthenticationPolicyId |
String | Optional | Mutable | If you set the action parameter to MFA, use mfaAuthenticationPolicyId to specify the ID of the MFA policy that should be used for authentication flows. |
result.mitigations[].mfaRegistrationPolicyId |
String | Optional | Mutable | If you set the action parameter to MFA, use mfaRegistrationPolicyId to specify the ID of the MFA policy that should be used for registration flows. |
result.mitigations[].verifyPolicyId |
String | Optional | Mutable | If you set the action parameter to VERIFY, use verifyPolicyId to specify the ID of the Verify policy that should be used. |
result.type |
String | Optional | Mutable | Can be one of two values: MITIGATION, MITIGATION_FALLBACK. When defining a mitigation, you must set result.type to MITIGATION. Policies that include mitigations must also include a fallback action. For the fallback action, result.type must be set to MITIGATION_FALLBACK. |
targets |
Object | Optional | Mutable | For targeted policies, used to define the conditions for applying the policy. |
targets.condition |
Object | Optional | Mutable | Used to specify the conditions for applying the policy - the type of flows, the user groups, and the applications that are being accessed. |
targets.condition.and |
Array | Optional | Mutable | Array of the conditions for applying the policy. It is mandatory to include in the array the relevant transaction types. The relevant user groups and applications are optional. Each element in the array contains the target transaction types/user groups/applications and the event attribute that is checked. |
targets.condition.and[].list |
Array | Optional | Mutable | Used to list the strings for the target transaction types, user groups, or applications, for example, ["AUTHENTICATION", "AUTHORIZATION"]. For transaction types, should contain one or more of the following: REGISTRATION,AUTHENTICATION,ACCESS,AUTHORIZATION,TRANSACTION. For user groups, should contain the name of one or more user groups. For applications, should contain the PingOne ID of one or more applications. |
targets.condition.and[].contains |
String | Optional | Mutable | The event attribute that is checked for the values specified in the list parameter. For transaction type, this should be set to ${event.flow.type}. For user groups, this should be set to ${event.user.groups}. For applications, this should be set to ${event.targetResource.id}. |
targets.condition.and[].type |
String | N/A | Read-only | Included in risk policy responses. For transaction types, value returned is STRING_LIST. For user groups, value returned is GROUPS_INTERSECTION. For transaction types, value returned is STRING_LIST. |
targets.condition.type |
String | N/A | Read-only | Included in risk policy responses for targeted policies. Value returned is AND if there is more than one condition, and value returned is VALUE_COMPARISON if there is only one condition. |
updatedAt |
Date | Required | Immutable | The date and time the resource was last updated (format ISO-8061). |
Risk policies events generated
Refer to Audit Reporting Events for the events generated.
Related topics
Create Risk Policy Set
Create Risk Policy Set - Targeted Policy with Mitigations
Create Risk Policy Set - Targeted Policy no Scores (PingID users)
Read Risk Policy Sets
Read Risk Policy Sets (with targeted policy order)
Read One Risk Policy Set
Reorder Targeted Risk Policies
Update Risk Policy Set
Delete Risk Policy Set
Risk Evaluations
When you define authentication or other flows for your users, you can include risk evaluations at relevant points in the flow. The risk evaluation that is carried out is based on the risk policy that you specify for the evaluation. The following diagram shows a simplified sample flow that includes risk evaluation.
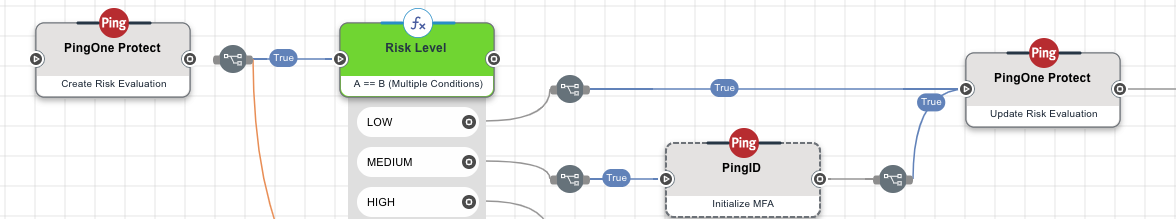
Note that the flow includes two distinct steps relating to risk evaluation.
The actual risk evaluation step should be added at a point in the flow where you would like to base the next action on the risk level calculated, for example, show an MFA prompt for medium or high-risk, but automatically grant access if the risk is deemed to be low.
After completion of the authentication steps, your flow should include a step to update the risk evaluation system with the results of the flow - was authentication completed successfully.
To ensure protection against fraudulent access attempts, it is essential that your flows include the SUCCESS/FAILED update step to indicate whether the flow was completed successfully or not. Many of the predictors used in risk policies are based on gradual learning of the characteristics of the access attempts made by your users, for example, where were they physically located and what operating system were they using. This learning process can only take place if your flows provide a clear indication which access attempts were made by legitimate users.
Risk evaluation data model
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
createdAt |
Date | N/A | Read-only | The time the resource was created (format ISO-8061). |
details |
Object | Optional | Mutable | Contains additional information about the risk evaluation. Refer to the following [Details data model]{#details-data-model} table. |
environment.id |
String | Required | Immutable | The environment resource's unique identifier. |
event |
Object | Required | Mutable | Contains the attributes identifying the event. For more information about event attributes, refer to the following [Event data model]{#event-data-model} table. |
id |
String | N/A | Read-only | The risk evaluation's unique identifier. |
riskPolicySet.id |
String | Optional | Mutable | The risk policy set's unique identifier. If this property and riskPolicySet.name are both specified, the policy set referenced by this property is used. If neither this property nor riskPolicySet.name are specified, the environment's default risk policy set is used. |
riskPolicySet.name |
String | Optional | Mutable | The risk policy set associated with this name. If this property and riskPolicySet.id are both specified, the policy set referenced by riskPolicySet.id is used. If neither this property nor riskPolicySet.id are specified, the environment's default risk policy set is used. |
riskPolicySet.targeted |
Boolean | Optional | Immutable | Set riskPolicySet.targeted to true if you want the risk evaluation to process the targeted policies defined in the environment rather than using a specific policy. The targeted policies are processed until a policy is found whose conditions (transaction type, user group, application) are met. |
result |
Object | N/A | Read-only | Contains the risk policy that evaluates as true. If there are several risk policies that evaluate as true, the highest priority risk policy is returned. If no risk policy evaluates as true, the defaultResult of the policy set is returned. |
result.level |
String | N/A | Read-only | The risk evaluation result level. Options are HIGH, MEDIUM, and LOW. |
result.recommendedAction |
String | N/A | Read-only | The recommended course of action based on the evaluation. Currently used only for policies that include a bot detection predictor, an Adversary-in-the-Middle (AitM) predictor, an email reputation predictor, or a traffic anomaly predictor. If recommendedAction is included in the response, the possible values are:
|
result.type |
String | N/A | Read-only | The risk evaluation result type. Options are VALUE, indicating any custom attribute that's defined. |
updatedAt |
Date | N/A | Read-only | The time the resource was last updated (format ISO-8061). |
Event data model
A POST request uses these properties to specify information about events processed for risk evaluation.
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
browser.cookie |
String | Optional | Mutable | To improve risk analysis, provide the value of a persistent cookie. |
browser.userAgent |
String | Optional | Mutable | The user agent string for the browser. |
completionStatus |
String | N/A | Read-only | The state of the evaluation transaction. In risk evaluation response, returned with a value of IN_PROGRESS. |
device |
Object | Optional | Mutable | Contains information about the device being used. |
device.externalId |
String | Optional | Mutable | If you want to maintain your own device IDs, you can send the device ID to the risk evaluation by using device.externalId, and this is the ID that will be used rather than the device ID provided by the Signals SDK. One situation where you may want to use this approach is if your mobile native app incorporates a WebView. In such cases, the mobile Signals SDK and the web Signals SDK will provide different device IDs. By providing your own device ID, you'll have a consistent device ID that can be used. |
evaluatedFactors.status |
String | Optional | Mutable | The state of the transaction. Options are FAILED, IN_PROGRESS, and SUCCESS. |
evaluatedFactors.type |
String | Optional | Mutable | The transaction type. |
flow.type |
String | Optional | Mutable | The type of flow for which the risk evaluation is being carried out. Can take any of the following values:
AUTHENTICATION. |
flow.subtype |
String | Optional | Mutable | If you want to provide additional detail about the context of the flow, you can specify a subtype in addition to type. The values that can be used for subtype are:
|
ip |
String | Required | Mutable | The originating IP address of the authentication flow. |
origin |
String | Optional | Mutable | The calling service. |
sdk |
Object | Optional | Immutable | Object used to provide the data from the Signals (Protect) SDK. |
sdk.signals.data |
String | Optional | Immutable | The data collected by the Signals (Protect) SDK. |
session.id |
String | Optional | Mutable | The unique session ID associated with the event. |
sharingType |
String | Optional | Mutable | The device sharing type. Options are UNSPECIFIED, SHARED, and PRIVATE. |
targetResource.id |
String | Optional | Mutable | The ID of the target application. |
targetResource.name |
String | Optional | Mutable | The name of the target application. |
user.groups |
String[] | Optional | Mutable | The names of the groups in which the user is a member. |
user.groups.name |
String | Optional | Mutable | The name of the group associated with the user (maximum size: 1024 characters). |
user.id |
String | Required/Optional | Mutable | The ID of the user associated with the event (maximum size: 1024 characters). Required when user.type is set to EXTERNAL. When user.type is set to PING_ONE, you must provide either user.id or user.name. |
user.name |
String | Required/Optional | Mutable | The name of the user associated with the event (maximum size: 1024 characters). When user.type is set to PING_ONE, you must provide either user.id or user.name. |
user.type |
String | Required | Mutable | The type of user associated with the event. The possible values are PING_ONE and EXTERNAL. |
Details data model
A POST request returns the following attributes in the details property for the specified event.
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
anonymousNetworkDetected |
Boolean | N/A | Read-only | Indicates whether the current authentication originated from an anonymous network (for example, proxy or VPN). |
city |
String | N/A | Read-only | The city related to the current transaction from the IP address. |
country |
String | N/A | Read-only | The country related to the current transaction from the IP address. |
detected |
Object | N/A | Read-only | Relevant only for Bot Detection predictors and Suspicious Device predictors. Contains the information on the rule that led to the level reported. |
detected.rule.id |
Integer | N/A | Read-only | Relevant only for Bot Detection predictors and Suspicious Device predictors. ID number of the rule that led to the level reported. |
device |
Object | N/A | Read-only | Contains information about the device being used. |
device.agent |
Object | N/A | Read-only | For risk evaluations that include the PingID Device Trust predictor, contains the data from the trust agent. |
device.agent.customScript.exitCode |
Integer | N/A | Read-only | If a local script was specified when installing the Workforce Trust agent on individual computers, will contain the exit code for the script. |
device.agent.customScript.output |
String | N/A | Read-only | If a local script was specified when installing the Workforce Trust agent on individual computers, will contain the output of the script. |
device.agent.id |
String | N/A | Read-only | The ID generated by the agent to identify the user's computer. |
device.agent.loggedInUser.domainName |
String | N/A | Read-only | The domain name for the logged-in user. |
device.agent.loggedInUser.name |
String | N/A | Read-only | The name of the logged-in user. |
device.agent.loggedInUser.objectSid |
String | N/A | Read-only | The SID (security identifier) for the logged-in user. |
device.agent.macAddress |
Array | N/A | Read-only | The MAC addresses of the user's computer. |
device.agent.name |
String | N/A | Read-only | The name of the user's computer. |
device.agent.os.name |
String | N/A | Read-only | The operating system on the user's computer. |
device.agent.os.version |
String | N/A | Read-only | The version of the operating system on the user's computer. |
device.agent.version |
String | N/A | Read-only | The version of the trust agent. |
device.estimatedDistance |
Double | N/A | Read-only | The distance between the current location of the device and the location of the device when the last risk evaluation was carried out. Distance is given in meters. |
device.externalId |
String | N/A | Read-only | The externally-maintained device ID that was provided in the risk evaluation request, if such an ID was included. For more details, refer to the Event data model. |
device.externalLastSeen |
Date | N/A | Read-only | If an externally-maintained device ID was provided in the risk evaluation request, externalLastSeen is the date and time that device was last seen. Returned only if the risk policy used for the evaluation includes the New Device predictor. |
device.id |
String | N/A | Read-only | The device ID provided by the Signals (Protect) SDK. |
device.lastSeen |
Date | N/A | Read-only | The date and time the device was last seen. Returned only if the risk policy used for the evaluation includes the New Device predictor. |
estimatedDistance |
Double | N/A | Read-only | The distance between the user's current location and the user location when a risk evaluation was last updated with the completion status SUCCESS. Distance is given in meters. |
estimatedSpeed |
Integer | N/A | Read-only | The speed the user would have had to travel at to reach their current location, based on the distance from the location when a risk evaluation for the user was last updated with the completion status SUCCESS and the time elapsed since that update event. Speed is given in kilometers per hour. |
impossibleTravel |
Boolean | N/A | Read-only | Indicates whether the distance between the location of the user in their previous successful authentication and current authentication infers that the user had to travel at a speed greater than 1000 kilometers per hour. This condition is marked as fulfilled, only if:
|
ipAddressReputation.domain.asn |
Integer | N/A | Read-only | The autonomous system number. |
ipAddressReputation.domain.isp |
String | N/A | Read-only | The ISP that registered the domain. |
ipAddressReputation.domain.organization |
String | N/A | Read-only | The organization that owns the domain. |
ipAddressReputation.domain.sld |
String | N/A | Read-only | The second-level domain. |
ipAddressReputation.domain.tld |
String | N/A | Read-only | The top-level domain. |
ipAddressReputation.level |
String | N/A | Read-only | The risk level of the evaluated IP address. Options are LOW, MEDIUM, and HIGH. If the score is less than 55, the level is LOW; if the score is greater than 77, the level is HIGH; if the score is between 55 and 77, the level is MEDIUM. Note that these guidelines could change based on data analytics and product consideration. If the ipAddressReputation.score is unknown, NULL is returned. |
ipAddressReputation.score |
Integer | N/A | Read-only | Represents the calculated score of the IP address involved in the transaction. Scores range between 0 and 100. A score of 0 indicates a non-risky IP address; a score of 100 indicates a high-risk IP address. If the IP address reputation score is not available for the specific IP address, NULL is returned. |
previousSuccessfulTransaction.anonymousNetworkDetected |
Boolean | N/A | Read-only | Indicates whether an anonymous network was detected. Information is available twenty-four hours after the last successful transaction. |
previousSuccessfulTransaction.city |
String | N/A | Read-only | The city of the IP address involved in the transaction. Information is available twenty-four hours after the last successful transaction. |
previousSuccessfulTransaction.country |
String | N/A | Read-only | The country of the IP address involved in the transaction. Information is available twenty-four hours after the last successful transaction. |
previousSuccessfulTransaction.ip |
String | N/A | Read-only | The IP address involved in the transaction. Information is available twenty-four hours after the last successful transaction. |
previousSuccessfulTransaction.state |
String | N/A | Read-only | The state of the IP address involved in the transaction. Information is available twenty-four hours after the last successful transaction. |
previousSuccessfulTransaction.timestamp |
String | N/A | Read-only | The timestamp of the transaction. Information is available twenty-four hours after the last successful transaction. |
state |
String | N/A | Read-only | The state or province related to the current transaction from the IP address. |
{{predictorCompactName}}.level |
String | N/A | Read-only | The risk score calculated for the predictor-related transactions associated with the accessing device, and for the current authentication attempt. Options are LOW, MEDIUM, and HIGH. |
{{predictorCompactName}}.reason |
String | N/A | Read-only | The reason (or reasons) provided for the risk score classification (for example, the operating system or browser type used by the device, and country in which the accessing device is located). Each reason is classified as Unusual, to indicate how much it deviates from normal user behavior, and its effect in calculating the overall predictor risk score. Note that these messages may change in the future. If you want to take action based on a certain scenario, the action should be based on the value of detected.rule.id, which is constant. |
{{predictorCompactName}}.status |
String | N/A | Read-only | Additional information about the predictor evaluation outcome. Example responses are NOT_AVAILABLE, IN_TRAINING_PERIOD, or FAILED_TO_COMPUTE. |
{{predictorCompactName}}.type |
String | N/A | Read-only | The type of the predictor. |
Update Risk Evaluation data model
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
completionStatus |
String | Required | Immutable | If the flow was completed successfully, set to SUCCESS. If not, set to FAILED. The value of this property can be changed only if its current state is IN_PROGRESS. |
Risk evaluations events generated
Refer to Audit Reporting Events for the events generated.
Response codes
| Code | Message |
|---|---|
| 200 | Successful operation. |
| 201 | Successfully created. |
| 400 | The request could not be completed. |
| 401 | You do not have access to this resource. |
| 403 | You do not have permissions or are not licensed to make this request. |
| 404 | The requested resource was not found. |
Providing feedback for risk evaluations
Use the riskFeedback endpoint to provide feedback on the accuracy of specific risk evaluations that were carried out. The request for providing feedback takes a list of feedback items, each consisting of the risk evaluation ID, a feedback category, and a reason for including it in that category (optional). In each such request, you can include feedback for up to 100 risk evaluations.
Risk evaluation feedback data model
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
evaluationFeedbackItems |
Array | Required | Immutable | The collection of feedback items. |
evaluationFeedbackItems[].feedbackCategory |
String | Required | Immutable | One of the following categories of feedback: FALSE_HIGH_RISK, FRIENDLY_BOT, NEW_ACCOUNT_FRAUD, COMPROMISED_ACCOUNT, AUTOMATED_ATTACK. |
evaluationFeedbackItems[].reason |
String | Optional | Immutable | The reason that the specific feedback category was specified. The possible values depend upon the category chosen.
|
evaluationFeedbackItems[].riskEvaluation.createdAt |
Date | Optional | Immutable | The date and time the risk evaluation was carried out. Use ISO-8061 format, for example, 2024-05-01T13:44:33.417Z. This parameter is optional, but providing a value for it makes the feedback process more efficient. |
evaluationFeedbackItems[].riskEvaluation.id |
String | Required | Immutable | The ID of the risk evaluation. |
Below is the sample body for a request that provides feedback on three risk evaluations. Full sample request can be found here.
{
"evaluationFeedbackItems":[
{
"riskEvaluation": {
"id": "15f1d245-33b3-4dba-849d-4df4b64b2d42"
},
"feedbackCategory": "FRIENDLY_BOT",
"reason": "INTERNAL_AUTOMATION"
},
{
"riskEvaluation": {
"id": "d1b638b4-638e-4c56-8fc6-872691c1bab1"
},
"feedbackCategory": "FALSE_HIGH_RISK",
"reason": "COMPANY_VPN"
},
{
"riskEvaluation": {
"id": "35f1d245-33b3-4dba-849d-4df4b64b2d45"
},
"feedbackCategory": "FALSE_HIGH_RISK"
}
]
}
Create Risk Evaluation
Create Risk Evaluation (using targeted risk policies)
Create Risk Evaluation (includes device trust predictor)
Create Risk Evaluation (with custom input)
Read One Risk Evaluation
Send Risk Evaluation Feedback
Update Risk Evaluation
Risk Predictors
PingOne supports multiple risk predictors, which are intended to identify possible fraudulent user behaviors based on these criteria:
-
Anonymous network detection
Malicious actors typically use anonymous networks, such as unknown VPNs, Tor, and proxies to mask their IP address. PingOne Protect analyzes IP address data from a user's device to determine if the address is originating from any type of anonymous network. If so, the user can be prompted for step-up authentication or denied access. PingOne Protect also supports creating a whitelist of networks, ensuring that legitimate VPN users can access authorized resources.
-
IP velocity
IP Velocity tracks the number of distinct IPs used per user. The threshold of the number of IPs per user is based on a statistical learning of the organization's past behavior. The risk predictor learns the mean average number of distinct IPs per user per unit of time (hour), and the standard deviation. The Risk Predictor then calculates the low, medium, and high thresholds of the number of IPs per user for the organization.
-
IP reputation
IP addresses that have been involved in malicious activities, such as distributed denial-of-service (DDoS) attacks or spam activity, are considered risky. The more frequently they are used for malicious activities, the higher their risk score. If a user attempts to access an application that is associated with an IP address previously involved with suspicious activity, the probability of potentially risky behavior increases. PingOne Protect analyzes data from different intelligence sources to determine the probability an IP address is associated with malicious activity and to request stronger authentication to verify the user's identity. It also supports creating a whitelist of networks, ensuring that legitimate VPN users can access authorized resources.
-
User velocity
User Velocity tracks the number of distinct users per IP. The threshold of the number of users per IP is based on a statistical learning of the organization's past behavior. The risk predictor learns the mean average number of distinct users per IP per unit of time (hour), and the standard deviation. The Risk Predictor then calculates the low, medium, and high thresholds of the number of users per IP for the organization.
-
User-based risk behavior
The user-based risk behavior predictor compares a transaction with the typical behavior of the specific user. For example, if a user accesses an application that they rarely use, user-based risk behavior detects an anomaly. User-based risk behavior is a machine-learning model that continuously updates. The machine-learning model characterizes abnormal activity as low, medium, or high risk.
-
Geovelocity anomaly
Users frequently sign on to the same application from multiple locations throughout the day. However, a time lapse between the current sign-on location and the previous location that is shorter than the time it would take to travel between the two points could indicate potentially suspicious activity. PingOne Protect analyzes location data to calculate if travel time between two session locations is physically possible. If the elapsed time is calculated to be impossible, the user can be prompted with step-up authentication or denied access. It also supports creating a whitelist of networks, ensuring that legitimate VPN users can access authorized resources.
-
User location anomaly
User Location Anomaly detects a user's login location and checks it against previously saved authentication locations. If an authentication attempt occurs at a location whose distance from the user's expected location is greater than the radius you defined, it is considered medium or high risk, depending on the extent of the deviation from the defined radius.
-
Bot detection
Analyzes multiple device and user behavior factors to detect non-human behavior, automated frameworks, and recorders during attempts to register or authenticate. This type of predictor requires use of the Signals (Protect) SDK.
-
New device
New device predictors allow your risk policy to take into account the risk associated with users trying to access applications from unknown devices or devices that have not been used for sign-on in the recent past.
-
Suspicious device
Checks for suspicious settings or mismatches between browser, operating system, and hardware attributes in order to detect situations such as emulators, superuser permissions, virtual machines, mirroring applications, and devices that have been tampered with. This type of predictor requires use of the Signals (Protect) SDK.
-
Adversary-in-the-Middle (AitM)
Adversary-in-the-Middle is a variant of Man-in-the-Middle attacks. In AitM, a malicious actor uses a reverse proxy to position themselves between a user and an online service in order to obtain user credentials and session tokens. This type of attack circumvents the protection usually provided by OTP-based multi-factor authentication, and is a common technique in phishing attempts. The predictor checks the domain name that the user is trying to access in order to identify AitM attacks. The AitM predictor requires use of the Signals (Protect) SDK.
-
Email reputation
Detects the use of disposable email addresses during registration. You can add the predictor to your risk policies, and you can also define a specific course of action if the
result.recommendedActionfield in the risk evaluation response indicates the use of a disposable email address. -
Traffic Anomaly
Intended for detection of traffic anomalies in terms of variables such as users, devices, and sessions, the Traffic Anomaly predictor will eventually include a variety of rules, some of which you can select to enable or disable. Currently, the predictor detects situations where there are a large number of risk evaluations requested for a single user within a short period of time, and optionally can also detect situations where the number of users per device during a given period is suspicious. When this predictor returns a value of High, it is recommended that you deny access because the suspicious activity is likely due to malicious behavior.
-
PingID Device Trust
The PingID Device Trust predictor checks if a device is trusted by validating the trust created during the installation of the PingID Device Trust agent. Requires use of the Signals (Protect) SDK and that the agent be installed on user computers.
-
Custom risk predictors
You can create custom predictors to assign high, medium, or low risk level based on external data that you provide or data that is accessible via the PingOne API but not included in the out-of-the-box predictor types.
In addition to the standard risk predictors, each of which represents a single risk factor, you can create composite risk predictors for situations where you are interested in combining a number of risk factors into a single predictor. For example, a situation where you are concerned about the use of an anonymous network only in cases where a user location anomaly is also reported.
Risk predictor evaluations
The evaluatedPredictors property in the policy set identifies the list of predictors (by ID) to be evaluated. If there is not enough data to assess a predictor level, the evaluation result does not assign any level to the predictor. In these cases, the response returns a Not enough information to assess risk score message.
When a predictor is added to a policy, regardless of the predictor weight, the predictor is evaluated when the policy is evaluated and its output appears in the details section of the risk service response. If you set the risk predictor's weight to 0, this predictor is evaluated but its risk assessment is not taken into account when calculating the risk score. Conversely, if the predictor is not added to the evaluatedPredictors property, or it was removed from the policy before evaluation, then the predictor is not evaluated and its output does not appear in the details section of the response.
Base risk predictor data model
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
activationAt |
Date | Optional | Mutable | For New Device predictors, you can use the activationAt parameter to specify a date on which the learning process for the predictor should be restarted. This can be used in conjunction with the fallback setting (default.result.level) to force strong authentication when moving the predictor to production. The date should be in the form yyyy-mm-dd. Note that activation date uses UTC time. |
compactName |
String | Required | Immutable | A unique name for the predictor. The value must be alpha-numeric (case-sensitive), with no special characters or spaces. This name is used in the API both for policy configuration, and in the Risk Evaluation response (under details). |
createdAt |
Date | N/A | Read-only | The date the risk predictor was created (format ISO-8061). |
default |
Object | Optional | Mutable | Contains the default values used for a new risk predictor. |
default.result |
Object | Optional | Mutable | Contains the result assigned to the predictor if the predictor could not be calculated during the risk evaluation. If this field is not provided, and the predictor could not be calculated during risk evaluation:
|
default.result.level |
String | Optional | Mutable | The default result level. Options are HIGH, MEDIUM, and LOW. |
default.result.type |
String | N/A | Read-only | The default result type. Options are VALUE, indicating any custom attribute that's defined. |
default.score |
Integer | N/A | Read-only | The score assigned to the risk predictor in a new policy by default. |
default.weight |
Integer | N/A | Read-only | The weight assigned to the risk predictor in a new policy by default. |
description |
String | Optional | Mutable | The description of the risk predictor. Maximum length is 1024 characters. |
detect |
String | Optional/Required | Immutable | Used only for New Device, Suspicious Device, and PingID Device Trust predictors. These predictor types all use the value DEVICE for type. The detect field is used to specify the kind of devices you are trying to detect. The possible values are NEW_DEVICE, SUSPICIOUS_DEVICE, and PINGID_TRUSTED_DEVICE. |
includeRepeatedEventsWithoutSdk |
Boolean | Optional | Mutable | Relevant only for Bot Detection predictors. Set the value of includeRepeatedEventsWithoutSdk to true to expand the range of bot activity that PingOne Protect can detect. |
name |
String | Required | Mutable | A unique, friendly name for the predictor. The name value is case (and space) sensitive. The API does not allow two predictors with the exact same name. However, the API does not restrict creating predictors with names such as my name and My Name. This name is displayed in the Risk Policies UI, when the admin is asked to define the overrides and weights. |
licensed |
Boolean | N/A | Read-only | Indicates whether the environment has the license required for the predictor. |
shouldDetectCompromisedAccount |
Boolean | Optional | Mutable | Relevant only for the User-based Risk Behavior predictor. Set shouldDetectCompromisedAccount to true if you want PingOne to attempt to detect compromised user accounts and take this into account when calculating the risk level for this predictor. |
shouldValidatePayloadSignature |
Boolean | Optional | Mutable | Relevant only for Suspicious Device predictors. If shouldValidatePayloadSignature is set to true, then any risk policies that include this predictor will require that the Signals SDK payload be provided as a signed JWT whose signature will be verified before proceeding with risk evaluation. You instruct the Signals SDK to provide the payload as a signed JWT by using the universalDeviceIdentification flag during initialization of the SDK, or by selecting the relevant setting for the skrisk component in DaVinci flows. |
type |
String | Required | Immutable | Any one of the following values: ADVERSARY_IN_THE_MIDDLE, ANONYMOUS_NETWORK, BOT, COMPOSITE, DEVICE, EMAIL_REPUTATION, GEO_VELOCITY, IP_REPUTATION, MAP, TRAFFIC_ANOMALY, USER_LOCATION_ANOMALY, USER_RISK_BEHAVIOR, VELOCITY. Note that the New Device, Suspicious Device, and PingID Device Trust predictors all use the type DEVICE. To differentiate between them, you use the detect field. For COMPOSITE, refer also to the Composite risk predictor data model below. For MAP, refer also to Custom risk predictors below. For VELOCITY, refer also to Velocity risk predictor data model below. For TRAFFIC_ANOMALY, refer also to Traffic anomaly risk predictor data model below. |
updatedAt |
Date | N/A | Read-only | The date the risk predictor set was updated (format ISO-8061). |
whiteList |
List[] | Optional | Mutable | For the geoVelocity, ipReputation, and anonymousNetwork predictors, use whiteList to specify IP addresses (CIDRs) that should be ignored by the predictor (usually because these are IPs you know are legitimate). The list can include IPs in IPv4 format and IPs in IPv6 format. For the ADVERSARY_IN_THE_MIDDLE predictor, use whiteList to specify the legitimate domains that your users will access for your restricted resources. |
Composite risk predictor data model
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
compositions |
Array | Required | Mutable | Contains the objects that specify the conditions to test and the risk level that should be assigned if the conditions are met. The array can contain a maximum of three elements. |
compositions[].condition |
Object | Required | Mutable | Specifies the set of conditions that are to be tested. |
compositions[].level |
String | Required | Mutable | The risk level that should be assigned if the specified conditions are met. Can be HIGH, MEDIUM, or LOW. |
Traffic anomaly risk predictor data model
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
rules |
Array | Required | Mutable | Collection of rules to use for this traffic anomaly predictor. |
rules[].enabled |
Boolean | Required | Mutable | Set to true to use the defined rule in the predictor. |
rules[].interval |
Object | Required | Mutable | Object that contains the fields used to define the timeframe to consider. The timeframe can be between 1 hour and 14 days. |
rules[].interval.unit |
String | Required | Mutable | The time unit for defining the timeframe for tracking number of users on the device - can be DAY or HOUR |
rules[].interval.quantity |
Integer | Required | Mutable | The number of days or hours for the timeframe for tracking number of users on the device. |
rules[].threshold |
Object | Required | Mutable | Object that contains the fields used to define the risk thresholds. |
rules[].threshold.medium |
Integer | Required | Mutable | Number of users during the defined timeframe that will be considered Medium risk. |
rules[].threshold.high |
Integer | Required | Mutable | Number of users during the defined timeframe that will be considered High risk. |
rules[].type |
String | Required | Mutable | The type of rule. Currently the only valid value is UNIQUE_USERS_PER_DEVICE - for tracking the number of unique users for a device over a defined timeframe. |
Velocity risk predictor data model
| Property | Type | Required? | Mutable? | Description |
|---|---|---|---|---|
by |
List | Optional | Mutable | An ordered list of JSON parameters for the values to aggregate. For example, ${event.ip},${event.user.id}. |
of |
String | Optional | Mutable | A JSON pointer for the value to aggregate. For example ${event.ip} or ${event.user.id}. |
threshold |
Object | Optional | Mutable | Contains information about the calculated threshold used. |
threshold.high |
Integer | Optional | Mutable | The value calculated for the high threshold. If the IP was accessed by more than the high number of users during the past hour, the IP is flagged as a HIGH userVelocityByIp.level. |
threshold.medium |
Integer | Optional | Mutable | The value calculated for the medium threshold. If the IP was accessed by more than the medium number of users during the past hour, the IP is flagged as a MEDIUM userVelocityByIp.level |
threshold.source |
String | Optional | Mutable | The source used to calculate the threshold. This can be:
|
threshold.calculatedAt |
Date | Optional | Mutable | The timestamp for the calculated threshold. |
threshold.expiresAt |
Date | Optional | Mutable | Indicates when the threshold will be recalculated. The recalculation will happen before this time. |
velocity.distinctCount |
Integer | Required | Mutable | The distinct count during a specified number of seconds. The duration is set using the velocity.during property. Applicable only for IP velocity predictors that have measure=DISTINCT_COUNT set. |
velocity.during |
Integer | Required | Mutable | The number of seconds for the DISTINCT_COUNT duration. Applicable only for IP velocity predictors that have measure=DISTINCT_COUNT set. |
Risk predictors events generated
Refer to Audit Reporting Events for the events generated.
Custom risk predictors
You can define three types of custom risk predictors:
- IP Range - for custom handling of IP-related risks
- String Matching - definition of risk levels associated with different values of custom input provided as a string
- Numeric Range - definition of risk levels associated with different values of custom input provided as a number
While different fields are used for defining these three types of conditions, the basic JSON structure for the body of the request is similar for all types:
- The top-level field
typemust be set to MAP. - The conditions are contained inside objects called
map.high,map.medium, andmap.low. You do not have to include all three levels, you just have to include at least one of these objects. If you include more than one level, for example,map.highandmap.medium, each must refer to the same variable, for example,${details.country}. - The
containsfield in the condition can use any of the following as the variable whose value is being checked:- Any field in the
detailsobject (refer to Risk Evaluations) - Any field in the
eventobject (refer to Risk Evaluations) - Any custom attribute added to the
eventobject simply by adding the attribute to theeventobject in the body of a risk evaluation request
- Any field in the
IP Range custom predictor - sample request body
{
"name": "Device IP - custom",
"compactName": "deviceIpCustom",
"map": {
"high": {
"ipRange": [
"1.1.1.1/5",
"2.2.2.2/8"
],
"contains": "${event.ip}"
}
},
"type": "MAP",
"default": {
"result": {
"level": "MEDIUM"
}
}
}
String Matching custom predictor - sample request body
{
"name": "Device country - custom",
"compactName": "deviceCountryCustom",
"map": {
"high": {
"list": [
"Iran",
"Syria"
],
"contains": "${details.country}"
},
"medium": {
"list": [
"Ethiopia",
"Russia"
],
"contains": "${details.country}"
}
},
"type": "MAP",
"default": {
"result": {
"level": "MEDIUM"
}
}
}
Numeric Range custom predictor - sample request body
{
"name": "Device Network Location",
"compactName": "deviceNetworkLocation",
"map": {
"high": {
"between": {
"minScore": 804672,
"maxScore": 12742000
},
"contains": "${details.device.estimatedDistance}"
},
"medium": {
"between": {
"minScore": 321869,
"maxScore": 804672
},
"contains": "${details.device.estimatedDistance}"
},
"low": {
"between": {
"minScore": 0,
"maxScore": 321869
},
"contains": "${details.device.estimatedDistance}"
}
},
"type": "MAP",
"default": {
"result": {
"level": "LOW"
}
}
}
Composite risk predictors
The JSON content below shows the body of a request for creating a composite predictor.
Details to note about the content of the request body:
-
typemust be set to COMPOSITE. -
Each of the objects in the
compositionsarray contain aconditionobject, which is use to specify the set of conditions to test, and thelevelfield, which specifies the risk level that should be assigned if the conditions are met. -
The
compositionsarray can contain a maximum of three elements. -
The specific predictor comparisons to carry out should use the
${details.*.level}format to specify the predictor to use. The string betweendetailsandlevelshould be the compact name of the predictor. -
In addition to standard and custom predictors, you can include the following risk factors in composite predictors: country (
${details.country}), state (${details.state}), IP range (${event.ip}), IP domain organization (${details.ipAddressReputation.domain.organization}), ISP (${details.ipAddressReputation.domain.isp}), target resource (${event.targetResource.name}), user ID (${event.user.id}), and user name (${event.user.name}). When creating conditions with these risk factors, you can use the following comparisons:equalsnotEqualscontains- to check if a value is in a defined list or in an IP rangenotContains- to check if a value is not included in a defined list or in an IP rangestartsWith- to check if a value begins with the specified string. Can be used with ISP, IP domain organization, user ID, and user name.endsWith- to check if a value ends with the specified string. Can be used with ISP, IP domain organization, user ID, and user name.containsIgnoreCase- to check if a value contains the specified substring, not case-sensitive. Can only be used for user ID and user name.
-
In your composite predictors you can also include conditions that check what user groups the user belongs to. For user groups conditions, the comparisons to use are
containsandnotContains. -
Use
${details.counters.predictorLevels.high},${details.counters.predictorLevels.medium}, and${details.counters.predictorLevels.low}to specify criteria relating to the number of predictors in a policy that yield a high, medium, or low risk result. For criteria of this type, use the relational termsequals,greater,lower,greaterEquals,lowerEquals. -
Within
conditionobjects, useorfor the array of conditions if it is enough for any of the conditions to be true, andandif all the criteria must be true. If none of the criteria can be true, construct anorarray, then enclose it in anotobject.
Example ofor:
"compositions": [
{
"condition": {
"or": [
{
"equals": 3,
"value": "${details.counters.predictorLevels.high}",
"type": "VALUE_COMPARISON"
},
{
"equals": "HIGH",
"value": "${details.anonymousNetwork.level}",
"type": "VALUE_COMPARISON"
},
{
"type": "STRING_LIST",
"list": [
"Italy",
"Germany"
],
"notContains": "${details.country}"
}
]
},
"level": "HIGH"
}
]
Example of not:
"compositions": [
{
"condition": {
"not": {
"or": [
{
"value": "${details.counters.predictorLevels.high}",
"equals": 3,
"type": "VALUE_COMPARISON"
},
{
"value": "${details.anonymousNetwork.level}",
"equals": "high",
"type": "VALUE_COMPARISON"
},
{
"list": [
"ITALY",
"GERMANY"
],
"notContains": "${details.country}",
"type": "STRING_LIST"
}
]
}
},
"level": "HIGH"
}
]
Full composite predictor example:
{
"name": "Composite - anonymous network and country",
"compactName": "compositeAnonymousAndCountry",
"licensed": true,
"compositions": [
{
"condition": {
"or": [
{
"equals": 3,
"value": "${details.counters.predictorLevels.high}",
"type": "VALUE_COMPARISON"
},
{
"equals": "HIGH",
"value": "${details.anonymousNetwork.level}",
"type": "VALUE_COMPARISON"
},
{
"type": "STRING_LIST",
"list": [
"Italy",
"Germany"
],
"notContains": "${details.country}"
}
]
},
"level": "HIGH"
},
{
"condition": {
"and": [
{
"equals": "HIGH",
"value": "${details.userLocationAnomaly.level}",
"type": "VALUE_COMPARISON"
}
]
},
"level": "MEDIUM"
}
],
"type": "COMPOSITE",
"default": {
"weight": 5,
"score": 50,
"result": {
"level": "LOW",
"type": "VALUE"
}
}
}
Deleting risk predictors
Create Risk Predictor (Custom - IP range)
Create Risk Predictor (Custom - string matching)
Create Risk Predictor (Custom - numeric range)
Create Risk Predictor (Composite with country)
Create Risk Predictor (Composite with country and user group)
Create Risk Predictor (Suspicious device)
Create Risk Predictor (Traffic anomaly)
Read All Risk Predictors
Read One Risk Predictor
Update Custom Risk Predictor
Update AITM Predictor
Delete Risk Predictor
Working with PingOne APIs
If you want to start building your own workflows with PingOne APIs, the Workflow Library provides step-by-step workflows with linked Postman collections to help you start using the PingOne APIs in your Postman environment. For information about how PingOne secures APIs, resources, and data, and what you can do to implement security measures for your PingOne deployment and applications, refer to Platform security.
PingOne API domains
This section discusses how PingOne API regional endpoints are entered in the domain name system (DNS). In DNS, and in our endpoints, the domain part of the uniform resource locator (URL) comprises three parts separated by periods, such as api.pingone.com: one of our service-specific subdomains, our PingOne domain name of pingone, and one of our top level domains.
We use Postman variables to manage this variety of domain parts in PingOne API endpoints. The later discussion is correct regarding the domain part that the variables evaluate to. However, to ease maintenance, the Postman environment template you get when you download a collection uses variables to isolate the TLD from the rest of the domain part and to isolate the domain part from the rest of the endpoint.
The environment template has a path variable for each subdomain. Each path variable uses another variable, {{tld}}, for the top level domain (TLD). Such as https://api.pingone.com/v1 for {{apiPath}}. The tld variable is first in the environment template that you downloaded.
The table below shows the top level domain value for each region. To change your region, simply change the default {{tld}} value from com to your region's TLD.
| Region | Code | Top level domain |
|---|---|---|
| North America region (excluding Canada) | NA | com (default) |
| Canada region | CA | ca |
| European Union region | EU | eu |
| Australia region | AU | com.au |
| Singapore region | SG | sg |
| Asia-Pacific region | AP | asia |
The PingOne API includes the following domains:
| Domain | Postman path variable | Description |
|---|---|---|
api.pingone.{{tld}}/v1 |
{{apiPath}} |
The primary domain for calling PingOne Management API resource server. Note: /v1 is required for {{apiPath}}. |
auth.pingone.{{tld}} |
{{authPath}} |
The authorization and authentication server domain called to request the access token required to authenticate PingOne API requests. Note: do not include /v1 for {{authPath}}. |
orchestrate-api.pingone.{{tld}}/v1 |
{{orchestratePath}} |
The primary domain for calling the PingOne DaVinci Management API resource server. Note: /v1 is required for {{orchestratePath}}. |
scim-api.pingone.{{tld}}/v1 |
{{scimPath}} |
PingOne API service for Cross-domain Identity Management (SCIM). Note: /v1 is required for {{scimPath}}. |
The {{...Path}} variable in the sample requests stand for the PingOne service endpoint. Refer to Public endpoints in the PingOne for Developers Foundations guide for more information.
The Try a Request feature
Our documentation for the PingOne APIs includes an interactive Try a Request feature. Try a Request enables you to configure and send a PingOne API request and get a response from within the documentation. This is a quick way to interactively test a PingOne API request without needing to use either Postman or the command line.
Requests in Authentication and Authorization APIs do not have the Try a Request feature due to a Cross-Origin Resource Sharing (CORS) constraint.
Calling the PingOne APIs from the command line
Each PingOne API request in the documentation includes an example request and response. By default, the example request is displayed using cURL. However, a number of coding languages are available in the associated drop-down list. If you want to run a request from the command line, you can select the coding language and copy the displayed request. You'll need to replace any variables in the request with the appropriate values before running the request.
Using Postman collection-level authorization
Most APIs require authorization to ensure that client requests access data securely. Postman can pass along whatever authorization details necessary for the method demanded by the endpoint. You can manually include authorization data in the header, body, or as parameters to a request. However, the easiest way is to use the Authorization tab in Postman. Select an authorization Type on that tab and Postman offers a dialog to gather the information required by that Type. When you run a request, Postman uses the information from the Authorization tab to automatically add the necessary authorization header, body, or parameters to the request. Postman offers the Authorization tab on requests, folders, and collections.
In PingOne collections, the authorization method is defined at the collection level. Only those requests that require a specific authorization method have authorization defined on the request (roughly 10% of PingOne requests). This allows you to easily change the authorization used for most requests. Refer to Postman Collection-Level Authorization for more information.
Postman and the PingOne APIs
We use Postman to create our PingOne DaVinci Admin API docs, and have supplied our Postman collections for you to download. There's also an accompanying Postman Environment template already populated with the variables used in the collections.
If you aren't currently using Postman, you can install the free version. Refer to Download Postman to install Postman, either locally, or in your browser.
Refer to The PingOne Protect API Postman collections for the collections you can download or fork.
For more information about our Postman environment variables, refer to The PingOne Postman environment template.
You'll also find all of the Postman collections for our documented PingOne use cases in our Workflow Library.
The PingOne Postman collections
You can get the PingOne Protect API Postman collection by following either of these methods for retrieving a Postman collection into your workspace:
-
Fork the collection into your workspace. Postman retains an association between the source and your fork. If we update the source collection, you can pull those changes into the fork in your workspace.
-
Import the collection into your workspace. This is a one-time transfer and retains no association to the source collection.
To retrieve a collection
Refer to The PingOne Protect API collections on this page.
-
Click the collection's Run In Postman button.
-
At the prompt, click Fork Collection at the bottom of the dialog or click import a copy near the bottom of the dialog.

-
Follow the on-screen instructions to fork or import the collection. You're prompted to select a Postman workspace for the retrieved collection.
When you fork a Postman collection, you create a copy of it in a selected workspace. Forking a collection creates a linked version that synchronizes with its source collection. This synchronization is apparent when you click the three dots icon on the forked collection - you'll see Pull changes on the context menu. When you click Pull changes, Postman compares the fork to the source collection. If changes are available, you can pull those changes into your fork. If you also elect to watch the collection, you'll receive notifications when the source changes.
If you import a collection, a copy is created in the selected workspace with no link back to the source. The collection is static. This may be desirable for some use cases. For example, if you intend to keep and use only some requests in a collection, a link back to the source is not needed.
You're not limited to choosing one method or the other. You can fork a copy to track the source and import a copy for experimentation, if you like.
The PingOne Protect API collections
These Postman collections include requests for all create, read, update, and delete (CRUD) operations for the PingOne Protect APIs.
For more information about the Postman environment variables included when you download or fork one of our Postman collections, refer to The PingOne Postman environment template.
The PingOne Postman environment template
Our Postman collections use variables in the request URLs to specify the UUIDs for PingOne resources. When you click the Run in Postman button for a collection, these environment variables are included in your download or fork. Use these environment variables as a template to assign your PingOne resource UUIDs with the common variables used in many of the requests.
For more information about using Postman environments, refer to the following topic in the Postman documentation: Environments in Postman.
POST requests in the PingOne Protect API Postman collections that create a resource and return a resource ID include a Postman script. This script automatically adds a resource variable to your active Postman environment, and uses the newly created ID as the value.
For example, the following request creates a new Protect variable. This request URL contains variables for the API path and environment ID:
POST {{apiPath}}/environments/{{envID}}/variables
To run this request, you must ensure the {{apiPath}} in the Postman environment template has the regional top-level domain (TLD) associated with your organization. Refer to Variables you must value for more information.
Almost every request in PingOne requires an environment ID. If you are working primarily in one environment for testing purposes, you'll want to add your environment's UUID to your active Postman environment as the value for the {{envID}} variable.
Requests to PingOne Management API endpoints require a valid access token to authenticate the request. In the PingOne Postman collections, the token value is represented in the Postman environment template as the variable {{accessToken}}.
With the {{tld}} and {{envID}} variables defined in your Postman template, and with a valid token value defined in the {{accessToken}} variable, you can run the request shown above:
POST {{apiPath}}/environments/{{envID}}/variables
If the request is successful, Postman adds a {{variableID}} variable to the current Postman environment automatically, and associates the new user's id property value (the UUID of the new user) with this variable.
Notes about environment variables and security
It's important to understand how Postman allows you to Store and reuse values using variables. Postman has two values for each environment variable: an Initial value and a Current value. You'll want to pay particular attention to differences between Initial and current values. Initial values are saved to Postman's cloud, and available to anyone who has access to the environment. Current values are saved only locally and available only to you. Postman uses only the current value in requests. If an environment variable has an initial value but no current value, Postman doesn't copy it to the current value or use the initial value in the request, the request simply fails. In this case, you need to manually copy the initial value to the current value.
When you create a new variable with an initial value and save the environment, Postman autofills the current value. However, that is the only time that Postman autofills the current value. If you subsequently delete the current value, the variable is no longer valued in a request.
Saving initial values to the Postman cloud impacts security. These initial values are available to anyone who has access to the workspace. If a workspace is public, you have a security issue.
Postman's recommended solution to exposing secrets is to Store secrets in your Postman Vault. Remember that Postman uses only current values in requests.
Variables you must value
When you download or fork a PingOne Postman collection, your workspace receives a set of Postman environment variables for you to use as a template. The variables that represent a resource in PingOne automatically receive a value when you create a new PingOne resource using Postman. Our script associated with the request (shown on the request's Scripts tab) inserts the identifier of the resource it creates as the value of the variable associated with that resource. However, some variables essential to using Postman with PingOne do not have their values inserted automatically. You must manually add the correct value to these variables before making any requests in Postman:
| Postman variable | PingOne resource |
|---|---|
adminAppID |
The Client ID of the Worker app you created Create an admin Worker app connection. |
adminAppSecret |
The Client Secret of the Worker app created. |
adminEnvID |
The ID for the environment in which your Worker app resides. |
envID |
The ID for the environment in which you are running your Postman API requests. |
orgID |
The ID for your organization. In the PingOne admin console, select Environment and click Properties to view your organization ID. |
tld |
The top-level domain to use for your environment. This is used in URLs containing apiPath, authPath, orchestratePath, and scimPath. |
apiPath |
The regional domain for the PingOne management server (https://api.pingone.{{tld}}/v1). |
authPath |
The regional domain for the PingOne authorization and authentication server (https://auth.pingone.{{tld}}). |
orchestratePath |
The regional domain for the PingOne DaVinci management server (https://orchestrate-api.pingone.{{tld}}/v1). |
scimPath |
The regional domain for the PingOne SCIM management server (https://scim-api.pingone.{{tld}}). |