Overview
The PingFederate PingID SDK IDP Adapter enables integration with the PingFederate Authentication API for end-user interactions, for step-up authentication and transaction approval. The PingFederate Authentication API provides access to the current state of the flow as an end user steps through a PingFederate authentication policy. For more information on the PingFederate Authentication API, see Authentication API in the PingFederate documentation.
Prerequisites
The PingFederate PingID SDK IDP Adapter supports integration with PingFederate Authentication API from the following software versions:
- PingFederate 9.3+
- PingFederate PingID SDK IDP Adapter 1.7+ for web authentication
- PingFederate PingID SDK IDP Adapter 1.8+ for web authentication and mobile pairing and authentication
Admins must follow the installation and configuration steps in the PingID admin guide:
PingFederate includes an API Explorer, which allows you to view the states, actions, and models available for the various API-capable adapters and selectors included in your PingFederate environment. For more details, see Exploring the authentication API in the PingFederate documentation.
Flow logic
The following examples illustrate the implementation of typical authentication flows with the PingID SDK adapter and the PingFederate Authentication API.
Web authentication flows
-
Email authentication flow example
This flow depicts an access request via a web browser, and MFA via an email OTP:
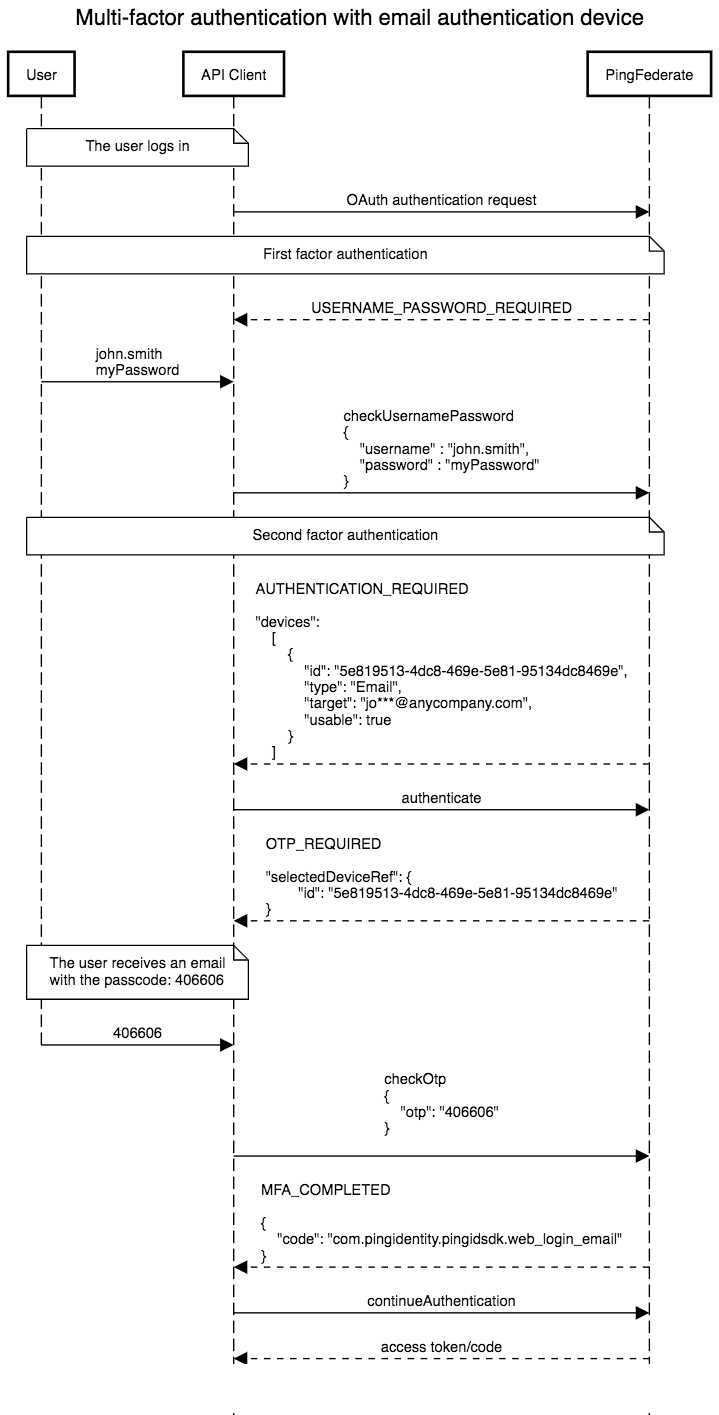
MFA for an OTP via email as depicted in the diagram above, and using the PingFederate Authentication API, follows the following logic flow:
- The user completes first-factor authentication. Completion of first-factor authentication is a prerequisite before progressing to MFA, when using the PingFederate PingID SDK IDP Adapter with the PingFederate Authentication API flow.
- The status of
AUTHENTICATION_REQUIREDtogether with thedevicesobject are returned in the response to the API client. - The API client invokes the
authenticateaction. - The status of
OTP_REQUIREDtogether with theselectedDeviceRefobject are returned in the response to the API client. In parallel, the user receives an email containing the OTP for authentication. - After the user has entered the OTP, the API client invokes the
checkOtpaction, submitting the OTP value to PingFederate. - On successful completion of MFA, PingFederate returns the status of
MFA_COMPLETEDto the API client. - The API client invokes the
continueAuthenticationaction. The API client must callcontinueAuthenticationin order to progress in the OIDC flow, and to complete it. - PingFederate returns an access token for SSO, to the API client.
-
Mobile application authentication flow example
This flow depicts an access request via a web browser, and MFA via mobile application:
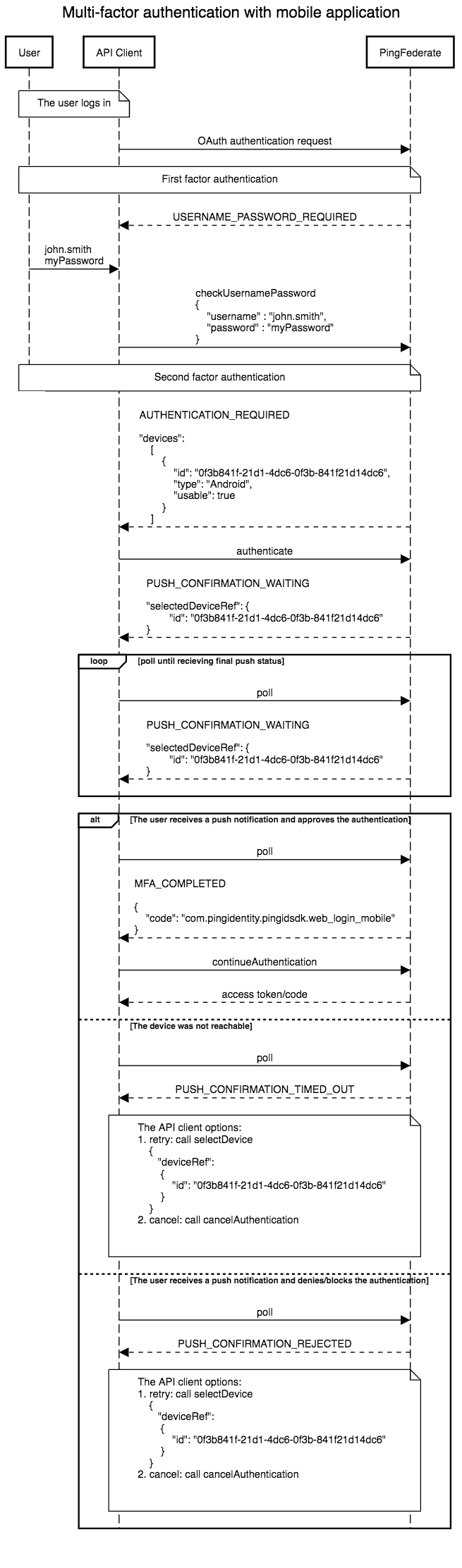
MFA for a mobile application as depicted in the diagram above, and using the PingFederate Authentication API, follows the following logic flow:
-
The user completes first-factor authentication. Completion of first-factor authentication is a prerequisite before progressing to MFA, when using the PingFederate PingID SDK IDP Adapter with the PingFederate Authentication API flow.
-
The status of
AUTHENTICATION_REQUIREDtogether with thedevicesobject are returned in the response to the API client. -
The API client invokes the
authenticateaction. -
The status of
PUSH_CONFIRMATION_WAITINGtogether with theselectedDeviceRefobject are returned in the response to the API client. -
The API client invokes the
pollaction, so that PingFederate gets the status of the mobile push. This is repeated until either a successful status is received or a timeout is reached. -
One of the following alternative statuses is reached:
MFA_COMPLETED:- The user receives a push notification and approves the authentication.
- The API client invokes the
continueAuthenticationaction. The API client must callcontinueAuthenticationin order to progress in the OIDC flow, and to complete it. - PingFederate returns an access token for SSO, to the API client.
PUSH_CONFIRMATION_TIMED_OUT:- The device was not reachable.
- There are two options available via the API client:
- Retry by calling
selectDevicewith thedeviceRefobject.
- Cancel the authentication request by calling
cancelAuthentication.
- Retry by calling
PUSH_CONFIRMATION_REJECTED:- The user receives a push notification, but denies or blocks it.
- There are two options available via the API client:
- Retry by calling
selectDevicewith thedeviceRefobject. - Cancel the authentication request by calling
cancelAuthentication.
- Retry by calling
-
Mobile authentication flows
-
Pair first device
This flow depicts a user pairing a first device via a mobile application:
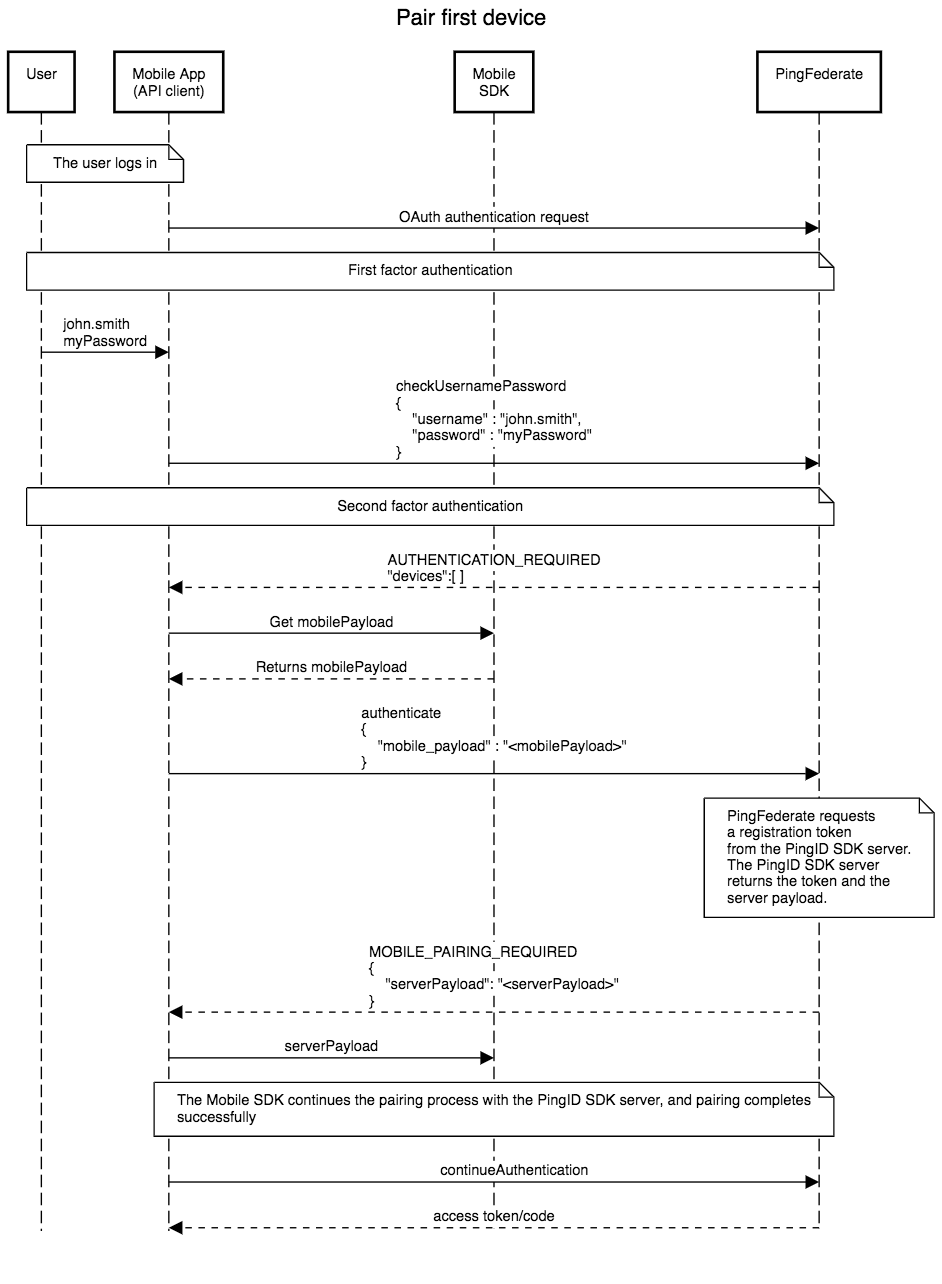
Pairing a first mobile device is depicted in the diagram above. This example uses the PingFederate Authentication API, and follows the following logic flow:
- The user completes first-factor authentication. Completion of first-factor authentication is a prerequisite before progressing to MFA, when using the PingFederate PingID SDK IDP Adapter with the PingFederate Authentication API flow.
- The status of
AUTHENTICATION_REQUIREDtogether with an emptydevicesobject are returned in the response to the Mobile app (API client). - The Mobile app (API client) gets a mobile payload from the mobile SDK.
- The Mobile app (API client) invokes the
authenticateaction, using the mobile payload. - The status of
MOBILE_PAIRING_REQUIREDtogether with theserverPayloadare returned in the response to the Mobile app (API client). - The Mobile app (API client) passes the
serverPayloadto the mobile SDK, in order to continue with the pairing process. - Once pairing is done, the Mobile app (API client) invokes the
continueAuthenticationaction. The Mobile app (API client) must callcontinueAuthenticationin order to progress in the OIDC flow, and to complete it. - PingFederate returns an access token to the Mobile app (API client).
-
Authorization with extra push verification for a paired mobile device
This flow depicts an access request via a mobile application, and authorization with extra push verification for a paired mobile device:
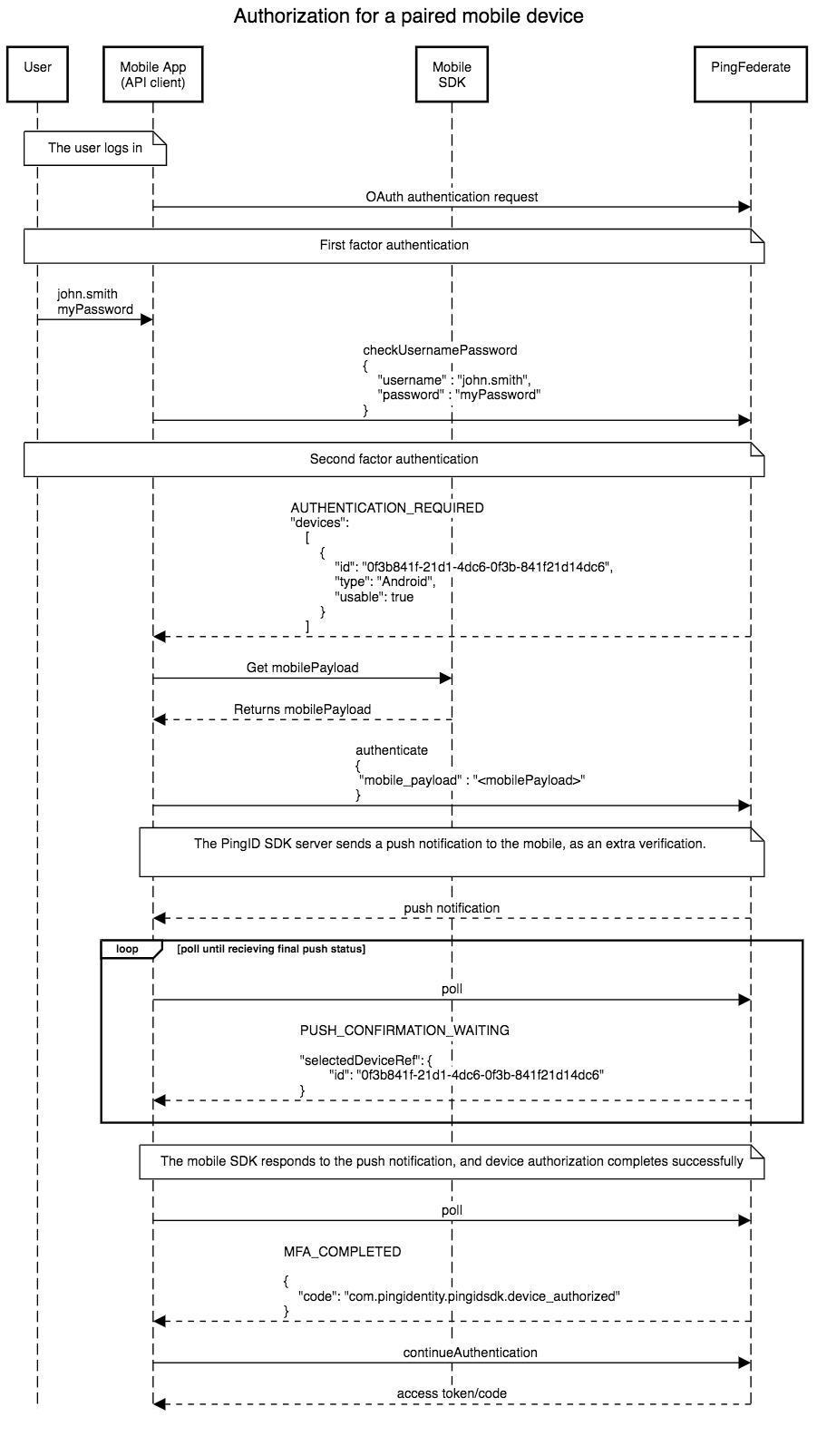
Authorization with extra push verification for a paired mobile device is depicted in the diagram above. This example uses the PingFederate Authentication API, and follows the following logic flow:
- The user completes first-factor authentication. Completion of first-factor authentication is a prerequisite before progressing to MFA, when using the PingFederate PingID SDK IDP Adapter with the PingFederate Authentication API flow.
- The status of
AUTHENTICATION_REQUIREDtogether with thedevicesobject are returned in the response to the Mobile app (API client). - The Mobile app (API client) gets a mobile payload from the mobile SDK.
- The Mobile app (API client) invokes the
authenticateaction, using the mobile payload. - The status of
PUSH_CONFIRMATION_WAITINGtogether with theselectedDeviceRefobject are returned in the response to the Mobile app (API client). - The Mobile app (API client) invokes the
pollaction, so that PingFederate gets the status of the mobile push. This is repeated until either a successful status is received or a timeout is reached. - The status of
MFA_COMPLETEDtogether with thedevice_authorizedcode are returned in the response to the Mobile app (API client). - The Mobile app (API client) invokes the
continueAuthenticationaction. The Mobile app (API client) must callcontinueAuthenticationin order to progress in the OIDC flow, and to complete it. - PingFederate returns an access token to the Mobile app (API client).
-
Login from unpaired mobile, and user has other paired mobile
This flow depicts an access request via an unpaired mobile application, and MFA via the user’s other paired mobile device. In the flow example, the
Additional Trusted Devicesparameter is set toVerify New Devices with Primary Devicein the PingID SDK IdP Adapter configuration in PingFederate. See Configure the PingID SDK adapter for PingFederate.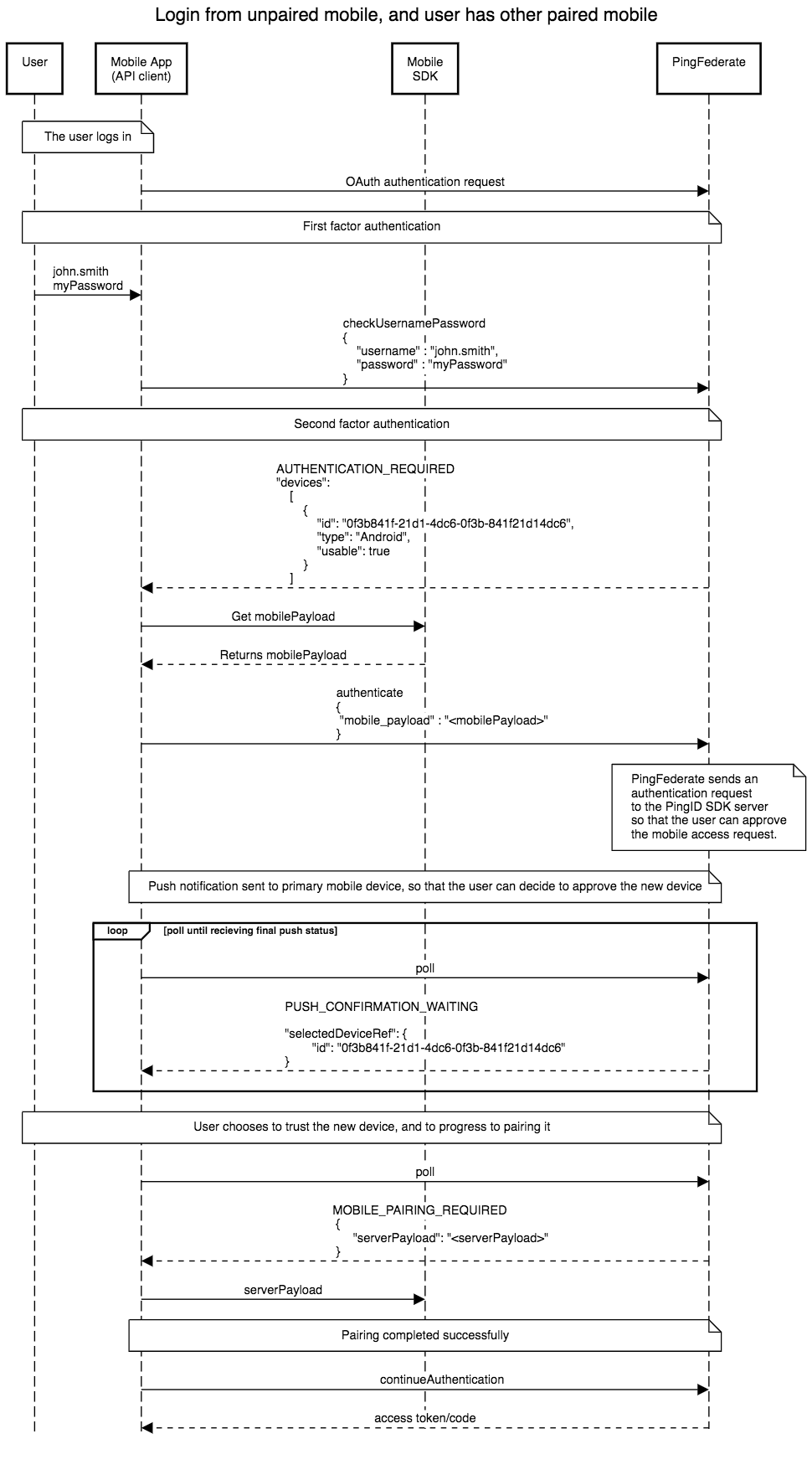
This diagram depicts an example of a login from an unpaired mobile, when the user has another paired mobile device. The
Additional Trusted Devicesparameter is set toVerify New Devices with Primary Devicein the PingID SDK IdP Adapter configuration in PingFederate. See Configure the PingID SDK adapter for PingFederate. This example uses the PingFederate Authentication API, and follows the following logic flow:- The user completes first-factor authentication. Completion of first-factor authentication is a prerequisite before progressing to MFA, when using the PingFederate PingID SDK IDP Adapter with the PingFederate Authentication API flow.
- The status of
AUTHENTICATION_REQUIREDtogether with thedevicesobject are returned in the response to the Mobile app (API client). The returned device is the user’s primary device. - The Mobile app (API client) gets a mobile payload from the mobile SDK.
- The Mobile app (API client) invokes the
authenticateaction, using the mobile payload. - The status of
PUSH_CONFIRMATION_WAITINGtogether with theselectedDeviceRefobject are returned in the response to the Mobile app (API client). The returned device is the user’s primary device. - A push notification is sent to primary mobile device so that the user can decide whether to trust the new device and continue the pairing flow.
- The Mobile app (API client) invokes the
pollaction, so that PingFederate gets the status of the mobile push. This is repeated until the user decides what to do with the unpaired device, or the user hasn’t responded. - Since the user decides to trust the device, the status of
MOBILE_PAIRING_REQUIREDtogether with theserverPayloadare returned in the response to the Mobile app (API client). - The Mobile app (API client) invokes the
continueAuthenticationaction. The Mobile app (API client) must callcontinueAuthenticationin order to progress in the OIDC flow, and to complete it. - PingFederate returns an access token to the Mobile app (API client).
PingID SDK state models
This table describes the PingID SDK state objects for the PingFederate Authentication API.
| Status | Response Model | Action | Description |
|---|---|---|---|
| AUTHENTICATION_REQUIRED | Indicates that authentication is required. This state is the first state returned from the adapter. If authentication is impossible for the user, the MFA_COMPLETED or MFA_FAILED states are returned with a corresponding code. Inactive users:
|
||
| DEVICE_SELECTION_REQUIRED | Indicates that device selection is required. This state is returned if no device was provided in the authenticate action, and device selection is required. Device selection is required when BOTH the following conditions occur:
|
||
| OTP_REQUIRED |
|
Indicates that OTP is required. This state is returned when the user is prompted to provide an OTP. The OTP is one of the following:
|
|
| PUSH_CONFIRMATION_WAITING |
|
Indicates that a push was sent to the user. Note: To get the final push confirmation state, the API client can either call the poll, or call GET |
|
| PUSH_CONFIRMATION_TIMED_OUT |
|
Indicates a push timeout state. | |
| PUSH_CONFIRMATION_REJECTED |
|
Indicates that the user has rejected the push. | |
| MFA_COMPLETED |
|
Indicates a successful MFA. The API client must call continueAuthentication in order to progress in the OIDC flow, and to complete it. |
|
| MFA_FAILED |
|
Indicates a dead end. The API client can proceed in the OIDC flow by calling cancelAuthentication. The adapter will return a FAILURE status. |
|
| MOBILE_PAIRING_REQUIRED |
|
Indicates that mobile pairing is required. |
PingID SDK action models
This table describes the PingID SDK action objects for the PingFederate Authentication API.
| Action | Request Model | Errors | Description |
|---|---|---|---|
| authenticate |
|
|
Starts an authentication flow. The mobile payload is required in cases of mobile app access. The presence or absence of the mobile payload detemines whether the flow is a mobile or web authentication, respectively. You cannot switch midway between mobile and web authentication flows. |
| selectDevice |
|
|
Starts an authentication with the specific deviceId. For example:{If there is already an authentication in progress, this authentication will be canceled. This action is available only when the user has at least one device, and can also be used as an authentication retry. A mobile payload is required if a user requests access from an untrusted mobile app, and needs to select of one of the user’s trusted devices to approve or deny access. |
| checkOtp |
|
|
Validates the provided OTP. A mobile payload is required if a user requests access from an untrusted mobile app, and is prompted to provide an OTP from another trusted device during the authentication process. |
| poll | This action has no model. | This action has no errors. | This action gets the status of the mobile push. An alternative is to call GET |
| cancelAuthentication | This action has no model. | This action has no errors. | This action cancels the current authentication step. |
| continueAuthentication | This action has no model. | This action has no errors. | This action continues the current authentication flow. |
Models inner objects
Device object
Representation of a device:
| Parameter name | Type | Description |
|---|---|---|
| id | String | Unique identifier of a trusted device in the PingID SDK server. |
| type | String | Device platform. Valid values:
|
| name | String | Model of the device, for example, iPhone 5S. This parameter is empty for OTP devices (SMS, voice, email). |
| nickname | String | The device’s nickname. |
| role | String | Role of the device in the user’s network: Valid values:
|
| enrollmentTime | Date | The date and time of the first registration of the device, in the context of the application. |
| applicationId | String | The ID of the PingID SDK customer mobile application. |
| bypassExpiration | Date | The date and time when the user’s device enabled bypass mode will expire. |
| bypassed | boolean | Indicates whether the user’s device is in bypass mode. |
| pushEnabled | boolean | Indicates whether the device can receive a push notification. |
| osVersion | String | The device’s operating system and version. |
| applicationVersion | String | The device’s application version. |
| target | String | The device’s masked email address/phone number. |
| usable | boolean | Indicates whether the device is usable. For example, if the device is locked, it is not usable. |
User object
Representation of a user:
| Parameter name | Type | Description |
|---|---|---|
| id | String | The user’s id. |
| firstName | String | The user’s first name. |
| lastName | String | The user’s last name. |
| status | String | The user’s status in PingID SDK. Possible values:
|
| lastLogin | Date | The last date and time the user authenticated successfully. |
ResourceRef object
Representation of a resource reference:
| Parameter name | Type | Description |
|---|---|---|
| id | String | The resource’s identifier. |
Error models
An error code is returned if the call flow state has not reached a dead end, and the user can still authenticate with a device. In cases where a flow reaches a dead end, the MFA_FAILED state is returned with a corresponding code.
Top level error codes
Detail level error codes
| Error code | Message | userMessageKey | Parent code |
|---|---|---|---|
| INVALID_OTP | An invalid or expired passcode was provided. | authn.api.invalid.otp | VALIDATION_ERROR |
| OTP_EXPIRED | The passcode has expired. | authn.api.otp.expired | REQUEST_FAILED |
| INVALID_DEVICE Note: This code is returned if the device is not one of the user’s devices, or if the device is unusable. |
An invalid device was provided. | VALIDATION_ERROR | |
| DEVICE_LOCKED | The device is locked. | authn.api.device.locked | REQUEST_FAILED |
| DEVICE_ROOTED | The user’s device is detected as having been rooted or jailbroken. | authn.api.device.rooted | REQUEST_FAILED |
| OTP_ATTEMPTS_LIMIT | The user performed too many unsuccessful passcode attempts. | authn.api.otp.attempts.limit | REQUEST_FAILED |
| OTP_RESEND_LIMIT | The user has resent the passcode the maximum number of times. See SMS and VOICE daily limits in Update a PingID SDK app’s configuration, in the admin guide. | authn.api.otp.resend.limit | REQUEST_FAILED |
| PUSH_FAILED | Failed to send the push message. | authn.api.push.failed | REQUEST_FAILED |
| INVALID_MOBILE_PAYLOAD | message (string): An invalid mobile payload was provided. | VALIDATION_ERROR |
MFA_FAILED codes
| Error code | Message | userMessageKey |
|---|---|---|
| SERVER_ERROR | Server error. | authn.api.server.error |
| SESSION_EXPIRED | Session expired. | authn.api.session.expired |
| SERVICE_UNAVAILABLE | Service unavailable. | authn.api.service.unavailable |
| USER_SUSPENDED | The user is suspended. | authn.api.user.suspended |
| INACTIVE_USER This error code indicates the user is inactive and the adapter does not support registration on the fly (“automatic pairing”). |
The user is inactive. | authn.api.inactive.user |
| UNABLE_TO_PAIR This error indicates that the user is inactive and the adapter cannot start the pairing process since the user must login from the mobile device application in order to register. |
Unable to pair. | authn.api.unable.to.pair |
| DEVICE_LOCKED This error code can also be returned if this is not a dead end. |
The device is locked. | authn.api.device.locked |
| OTP_RESEND_LIMIT This error code can also be returned if this is not a dead end. |
The user has re-sent the passcode the maximum number of times. | authn.api.otp.resend.limit |
| DEVICE_ROOTED This code can also be returned if this is not a dead end. |
The user’s device is detected as having been rooted or jailbroken. | authn.api.device.rooted |
| PUSH_FAILED | Failed to send the push message. | authn.api.push.failed |
| NO_RESPONSE_PASSIVE_PUSH | Mobile payload is valid but the extra push verification did not arrive. | authn.api.no.response.passive.push |
| DEVICE_BLOCKED | The device is blocked. | authn.api.device.blocked |