Most organizations have a traditional first factor authentication flow, in which the native application authenticates via an authentication server using the user’s username and password. Implementation of PingID SDK requires minimal changes to this paradigm.
Multifactor authentication (MFA) is a security measure that requires more than one method of authentication from independent categories of credentials, to verify the user’s identity for a login or for other transactions. A device (which can be a physical mobile device or an SMS, voice or email) must be paired with the PingID SDK server, in order for MFA to be performed.
QR code based authentication is a complementary method, which offers secure, passwordless authentication. QR code based authentication can effectively eliminate the need for first factor authentication. This method combines the strength of a strong secure authentication measure, with a streamlined user experience.
Supported multifactor authentication (MFA) methods
PingID SDK’s multifactor authentication mechanism includes:
- Mobile device authorization.
- Adding an out of band (OOB) MFA element to mobile based authentication.
- SMS, voice and email authentication.
- Transaction approval using PingID SDK.
- QR code based authentication.
MFA using the PingID SDK component
In PingID SDK, MFAs are implemented by the native mobile app’s PingID SDK component, creating and passing a payload to the customer server, and from there to the PingID SDK server. PingID SDK provides a configuration option for adding an extra out of band element of device verification. PingID SDK also supports transaction approval for application contexts which require elevated security.
Mobile device authorization
Device authorization is a seamless MFA, executed in the background, that does not influence the user experience. It’s comprised of a payload, a small packet of data that identifies the device, which is passed from the native application to the authentication server, and then onwards to the PingID SDK server. This enables performing MFA as part of the regular authentication flow, with minimal impact in terms of code changes and performance, and no impact on user experience.
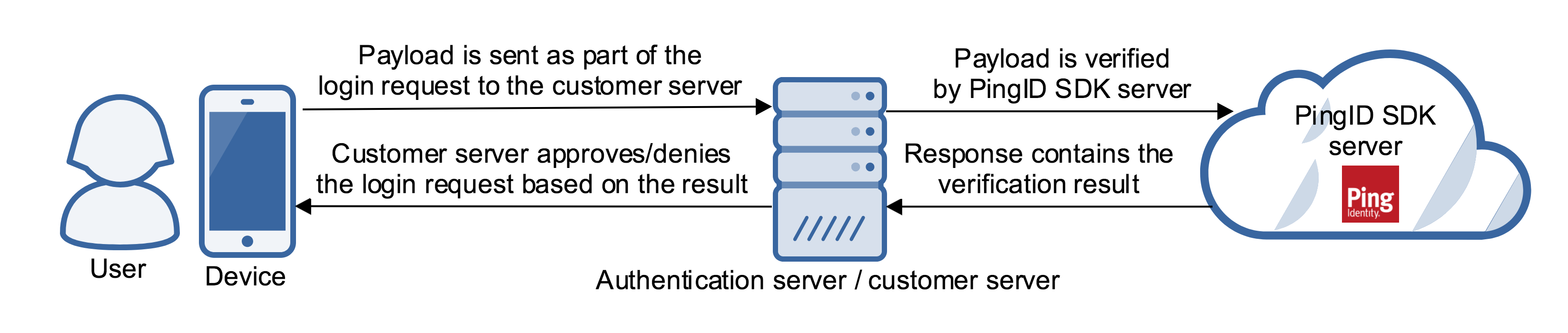
A payload is a string produced by the PingID SDK component for the customer mobile application.
- The customer mobile application passes the payload to the authentication server when the user logs into the application.
- The authentication server then passes the payload to the PingID SDK server in order to complete the MFA.
- The MFA verification result is returned to the authentication server, which in turn, uses the MFA verification result to approve or deny the device’s login request.
Adding an out of band (OOB) MFA element to mobile based authentication
Out of band (OOB) MFA is an optional extension to payload based MFA, so that it incorporates a separate communications channel to verify the user’s device. This makes it more difficult for fraudsters to bypass or tamper with the authentication process. Out of band MFA provides a superior level of security, which may add several seconds (a configurable timeout will be featured in the future) to the duration of the authentication flow.
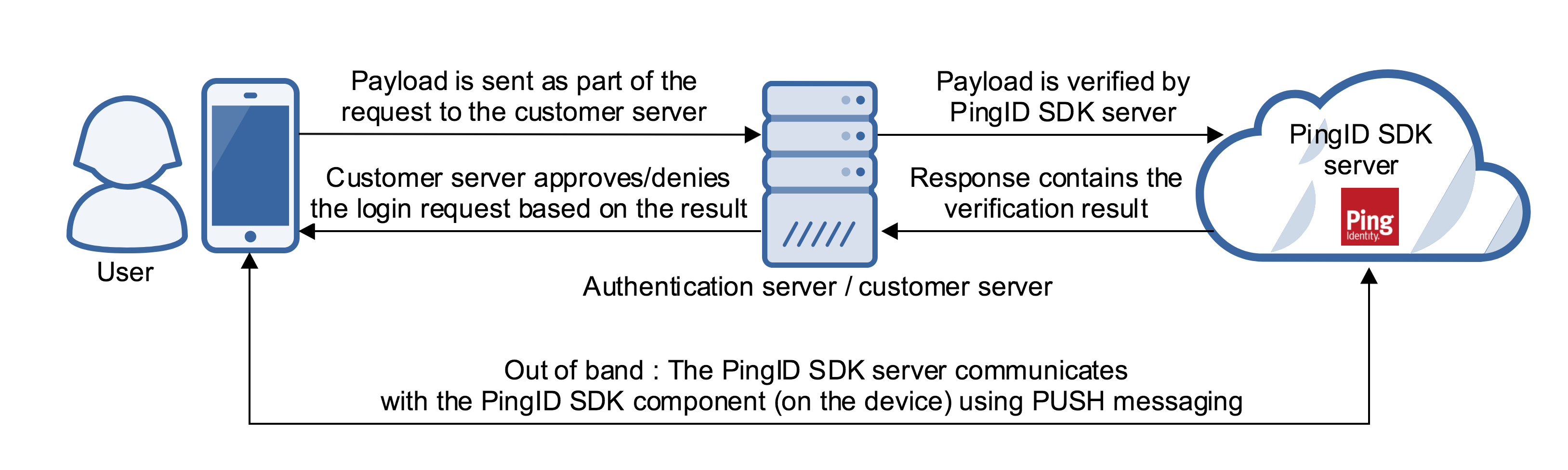
In PingID SDK, out of band authentication can be configured so that in parallel to the payload based verification, a push message will be sent (via FCM or APNS) to the device and will provide an additional authentication measure. The push mechanism is on the basis of “best effort”, meaning that if the push is not received or is not successful, the transaction is not canceled or denied. Rather, PingID SDK returns all the information to the customer server, whose logic will determine whether to cancel or deny the transaction, or alternatively, how to progress.
SMS, voice and email authentication
Some organizations may have customers who do not have a smart mobile device, or prefer not to download mobile apps on their mobile devices. In addition to mobile based authentication, PingID SDK supports the alternative usage of one time passcodes (OTPs) with customized message content sent to users via SMS, voice and email messages.
In contrast to a mobile device, SMS, voice and email devices may be considered as virtual devices, since the phone number or email address, rather than a physical device, is paired with a user and application. Phone numbers used for SMS or voice authentication may be ported from one mobile device to another, without affecting their paired PingID SDK status. Similarly, an address used for email authentication may be accessible on multiple physical devices, without affecting its paired PingID SDK status.
Transaction approval using PingID SDK
Transaction approval (also known as step up authentication) is elevated security for a high value or high risk resource or service, within the particular context of an application, which requires authentication using a higher assurance credential than previously required for general access of the application.
In some applications, it makes sense not to use the second factor authentication capabilities during the login process, but activate it during certain user actions, such as a payments or bank transfers. These actions are referred to as transaction approvals, as they elevate the user’s security context only when required by the business logic.
PingID SDK enables the developer to incorporate transaction approval flows and authentications into native applications quickly and easily. In PingID SDK, transaction approvals are regular authentications which are implemented in exactly the same way, and can be customized by the customer’s developer. A string containing information about the transaction can be sent as part of the authentication, and the native app can use it to show the transaction information, or to display different behavior during the authentication.
QR code based authentication
One of the major objectives of the QR code based authentication is to permit secure passwordless authentication. The customer server does not need advance knowledge of who the user is (for example, first factor authentication is not required).
The QR code based authentication follows the following flow:
- The customer server, or PingFederate PingID SDK adapter, displays a QR code image in the web browser, or a deep link in the mobile browser.
- The user scans the QR code with their trusted mobile device, and the mobile application passes it back to the PingID SDK server. QR code based authentication also supports authentication of multiple users who use the same device.
- The PingID SDK server validates the QR code.
- If the QR code is valid, the user is approved and authentication is completed.
- If extra verification is required, a silent push is sent to the device. In addition, a user approval message can also be sent to the user for additional user confirmation.